آسیبپذیریهای حیاتی هفته آخر فروردینماه

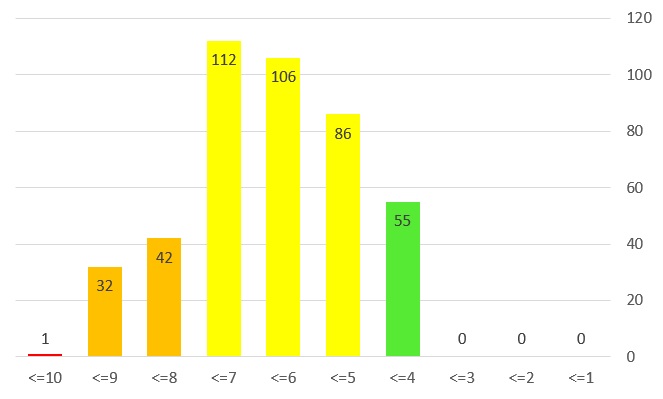
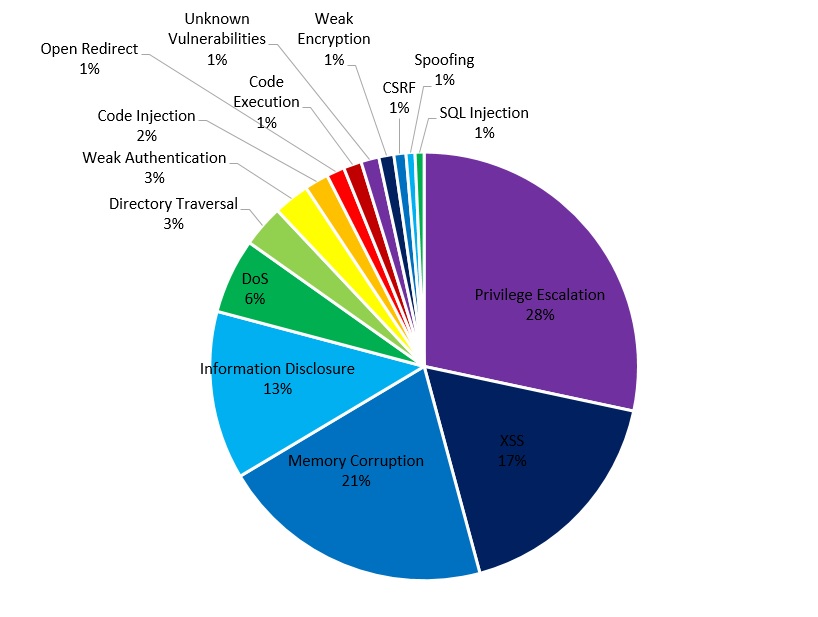
مهم ترین آسیبپذیری این هفته مربوط به محصولات گوگل و مایکروسافت است: آسیبپذیریهایی با سطح خطر « حیاتی» و «پرخطر». همچنین محصولات پرکاربرد شرکتهای مهمی چون اینتل، IBM و سیسکو همگی دارای آسیبپذیریهای «پرخطر» و «خطرناک» هستند. در محصولات VMware، Siemens وکرنل لینوکس نیز چندین آسیبپذیری «پرخطر» شناسایی شده است.
|
نوع آسیبپذیری |
محصول آسیبپذیر |
شناسه آسیبپذیری |
|
Information Disclosure |
Apple tvOS State Management |
CVE-2019-6203 |
|
Code Execution |
Autodesk Dynamo BIM Signature Validation |
CVE-2020-7079 |
|
Memory Corruption |
Autodesk FBX-SDK Code Execution |
CVE-2020-7080 |
|
Memory Corruption |
Autodesk FBX-SDK Heap-based |
CVE-2020-7085 |
|
Denial of Service |
Autodesk FBX-SDK Integer Overflow |
CVE-2020-7083 |
|
Denial of Service |
Autodesk FBX-SDK NULL Pointer Dereference |
CVE-2020-7084 |
|
Memory Corruption |
Autodesk FBX-SDK Type Confusion |
CVE-2020-7081 |
|
Memory Corruption |
Autodesk FBX-SDK Use-After-Free |
CVE-2020-7082 |
|
cross site request forgery |
Broadcom ProxySG/ASG Management Center |
CVE-2019-18376 |
|
Weak Authentication |
Broadcom ProxySG/ASG Management Interface |
CVE-2019-18375 |
|
Open Redirect |
CA API Developer Portal |
CVE-2020-11663 |
|
Privilege Escalation |
CA API Developer Portal Access Control |
CVE-2020-11659 |
|
Privilege Escalation |
CA API Developer Portal Access Control |
CVE-2020-11661 |
|
Privilege Escalation |
CA API Developer Portal Access Control |
CVE-2020-11666 |
|
Information Disclosure |
CA API Developer Portal Cross-Origin |
CVE-2020-11662 |
|
Open Redirect |
CA API Developer Portal homeRedirect Page |
CVE-2020-11664 |
|
Information Disclosure |
CA API Developer Portal |
CVE-2020-11660 |
|
Open Redirect |
CA API Developer Portal loginRedirect Page |
CVE-2020-11665 |
|
Privilege Escalation |
CA API Developer Portal |
CVE-2020-11658 |
|
Denial of Service |
Cisco Aironet Crash |
CVE-2020-3260 |
|
Denial of Service |
Cisco IoT Field Network Director Constrained Application Protocol |
CVE-2020-3162 |
|
Privilege Escalation |
Cisco IP Phone Web Server |
CVE-2020-3161 |
|
cross site request forgery |
Cisco Mobility Express Software Web-based Management Interface |
CVE-2020-3261 |
|
Directory Traversal |
Cisco UCS Director/UCS Director Express for Big Data REST API |
CVE-2020-3239 |
|
Directory Traversal |
Cisco UCS Director/UCS Director Express for Big Data REST API |
CVE-2020-3240 |
|
Directory Traversal |
Cisco UCS Director/UCS Director Express for Big Data REST API |
CVE-2020-3243 |
|
Directory Traversal |
Cisco UCS Director/UCS Director Express for Big Data REST API |
CVE-2020-3247 |
|
Directory Traversal |
Cisco UCS Director/UCS Director Express for Big Data REST API |
CVE-2020-3248 |
|
Directory Traversal |
Cisco UCS Director/UCS Director Express for Big Data REST API |
CVE-2020-3249 |
|
Directory Traversal |
Cisco UCS Director/UCS Director Express for Big Data REST API |
CVE-2020-3250 |
|
Directory Traversal |
Cisco UCS Director/UCS Director Express for Big Data REST API |
CVE-2020-3251 |
|
Directory Traversal |
Cisco UCS Director/UCS Director Express for Big Data REST API |
CVE-2020-3252 |
|
Directory Traversal |
Cisco Unified Communications Manager TAPS |
CVE-2020-3177 |
|
Privilege Escalation |
Cisco Webex Business Suite Man-in-the-Middle |
CVE-2019-1866 |
|
Privilege Escalation |
Cisco Webex Meeting Multimedia Viewer |
CVE-2020-3126 |
|
Denial of Service |
Cisco Wireless LAN Controller Control and Provisioning |
CVE-2020-3273 |
|
Denial of Service |
Cisco Wireless LAN Controller Control and Provisioning Restart |
CVE-2020-3262 |
|
Cross Site Scripting |
Climatix POL908/POL909 Persistent |
CVE-2020-7575 |
|
Cross Site Scripting |
Climatix POL908/POL909 Server Config Web Interface Persistent |
CVE-2020-7574 |
|
Privilege Escalation |
cpp-httplib Filter set_header |
CVE-2020-11709 |
|
Cross Site Scripting |
CyberSolutions CyberMail go |
CVE-2020-11734 |
|
Memory Corruption |
Cypress WICED Studio Bluetooth Low Energy dhmulp_getRxBuffer |
CVE-2019-13916 |
|
Weak Authentication |
DAViCal Andrew's Web Libraries Session Management |
CVE-2020-11728 |
|
Weak Authentication |
DAViCal Andrew's Web Libraries Session |
CVE-2020-11729 |
|
Command Injection |
Dell EMC Integrated Data Protection Appliance ACM |
CVE-2020-5350 |
|
Information Disclosure |
Dell EMC Networking X-Series |
CVE-2020-5330 |
|
Privilege Escalation |
D-Link DSL-GS225 J1 CLI OS |
CVE-2020-6765 |
|
Privilege Escalation |
docker-kong API Service |
CVE-2020-11710 |
|
Privilege Escalation |
Dungeon Crawl Stone Soup Lua crawlrc |
CVE-2020-11722 |
|
Memory Corruption |
Eaton HMiSoft VU3 HMIVU Runtime |
CVE-2020-10639 |
|
Memory Corruption |
Eaton HMiSoft VU3 HMIVU Runtime Out-of-Bounds |
CVE-2020-10637 |
|
Privilege Escalation |
eXtplorer |
CVE-2019-7305 |
|
Denial of Service |
FTPDMIN Crash |
CVE-2020-10813 |
|
Memory Corruption |
Fuji Electric V-Server VPR File Heap-based |
CVE-2020-10646 |
|
Information Disclosure |
GNOME Evolution |
CVE-2020-11879 |
|
Directory Traversal |
GNOME file-roller fr-archive-libarchive.c |
CVE-2020-11736 |
|
Memory Corruption |
GNU C Library Signal Trampoline backtrace |
CVE-2020-1751 |
|
Privilege Escalation |
Google Android AppOpsControllerImpl.java onOpActiveChanged |
CVE-2020-0080 |
|
Memory Corruption |
Google Android AssetManager.java finalize |
CVE-2020-0081 |
|
Memory Corruption |
Google Android CryptoPlugin.cpp decrypt_1_2 |
CVE-2020-0079 |
|
Memory Corruption |
Google Android DrmPlugin.cpp releaseSecureStops |
CVE-2020-0078 |
|
Privilege Escalation |
Google Android ExternalVibration.java ExternalVibration |
CVE-2020-0082 |
|
Information Disclosure |
Google Android FPC IRIS TrustZone App authorize_enroll |
CVE-2020-0077 |
|
Memory Corruption |
Google Android FPC IRIS TrustZone App get_auth_result |
CVE-2020-0076 |
|
Information Disclosure |
Google Android FPC IRIS TrustZone App set_shared_key |
CVE-2020-0075 |
|
Memory Corruption |
Google Android msm-cirrus-playback.c crus_afe_get_param |
CVE-2020-0068 |
|
Memory Corruption |
Google Android rw_t2t_ndef.cc rw_t2t_extract_default_locks_info |
CVE-2020-0071 |
|
Memory Corruption |
Google Android rw_t2t_ndef.cc rw_t2t_handle_tlv_detect_rsp |
CVE-2020-0072 |
|
Memory Corruption |
Google Android rw_t2t_ndef.cc rw_t2t_handle_tlv_detect_rsp |
CVE-2020-0073 |
|
Memory Corruption |
Google Android rw_t2t_ndef.cc rw_t2t_update_lock_attributes |
CVE-2020-0070 |
|
Information Disclosure |
Google Chrome Cache Cross-Origin |
CVE-2020-6442 |
|
Privilege Escalation |
Google Chrome Clipboard |
CVE-2020-6456 |
|
Privilege Escalation |
Google Chrome Content Security Policy |
CVE-2020-6445 |
|
Privilege Escalation |
Google Chrome Content Security Policy |
CVE-2020-6446 |
|
Memory Corruption |
Google Chrome Developer Tools Heap-based |
CVE-2020-6447 |
|
Privilege Escalation |
Google Chrome Developer Tools |
CVE-2020-6443 |
|
Memory Corruption |
Google Chrome DevTools Use-After-Free |
CVE-2020-6434 |
|
Information Disclosure |
Google Chrome Extensions |
CVE-2020-6440 |
|
Memory Corruption |
Google Chrome Extensions Use-After-Free |
CVE-2020-6454 |
|
Privilege Escalation |
Google Chrome Policy Enforcement |
CVE-2020-6432 |
|
Privilege Escalation |
Google Chrome Policy Enforcement |
CVE-2020-6433 |
|
Privilege Escalation |
Google Chrome Policy Enforcement |
CVE-2020-6435 |
|
Privilege Escalation |
Google Chrome Policy Enforcement |
CVE-2020-6438 |
|
Privilege Escalation |
Google Chrome Policy Enforcement |
CVE-2020-6439 |
|
Privilege Escalation |
Google Chrome Policy Enforcement |
CVE-2020-6441 |
|
spoofing |
Google Chrome Policy Enforcement spoofing |
CVE-2020-6431 |
|
Memory Corruption |
Google Chrome Use-After-Free |
CVE-2020-6423 |
|
Memory Corruption |
Google Chrome v8 Type Confusion |
CVE-2020-6430 |
|
Memory Corruption |
Google Chrome v8 Use-After-Free |
CVE-2020-6448 |
|
Memory Corruption |
Google Chrome WebRTC Heap-based |
CVE-2020-6444 |
|
Information Disclosure |
Google Chrome WebSQL Out-of-Bounds |
CVE-2020-6455 |
|
spoofing |
Google Chrome WebView spoofing |
CVE-2020-6437 |
|
Memory Corruption |
Google Chrome Window Management Use-After-Free |
CVE-2020-6436 |
|
Privilege Escalation |
Grandstream GXP1600 Interface upload_vpntar |
CVE-2020-5738 |
|
Privilege Escalation |
Grandstream GXP1600 Web Interface Command |
CVE-2020-5739 |
|
Privilege Escalation |
Hgiga C&Cmail Configuration |
CVE-2020-10511 |
|
SQL Injection |
Hgiga C&Cmail |
CVE-2020-10512 |
|
Information Disclosure |
Huawei Mate 30/Mate 30 Pro |
CVE-2020-1801 |
|
Privilege Escalation |
Huawei OSCA-550/OSCA-550A/OSCA-550AX/OSCA-550X |
CVE-2020-1802 |
|
Weak Authentication |
IBM QRadar Certificate Man-in-the-Middle |
CVE-2019-4654 |
|
Weak Encryption |
IBM QRadar Default Credentials |
CVE-2020-4269 |
|
Information Disclosure |
IBM QRadar Error Message |
CVE-2019-4593 |
|
Privilege Escalation |
IBM QRadar File Permission |
CVE-2020-4270 |
|
Information Disclosure |
IBM QRadar Man-in-the-Middle |
CVE-2019-4594 |
|
Privilege Escalation |
IBM QRadar Permission Check |
CVE-2020-4274 |
|
Privilege Escalation |
IBM QRadar |
CVE-2020-4271 |
|
Privilege Escalation |
IBM QRadar |
CVE-2020-4272 |
|
|
IBM QRadar Server-Side Request Forgery |
CVE-2020-4294 |
|
Privilege Escalation |
IBM QRadar SIEM |
CVE-2020-4151 |
|
Cross Site Scripting |
IBM QRadar Web UI |
CVE-2020-4268 |
|
Information Disclosure |
IBM TRIRIGA Application Platform Error Message |
CVE-2020-4277 |
|
Privilege Escalation |
IBM WebSphere Application Server SOAP Connector |
CVE-2020-4362 |
|
Privilege Escalation |
iCatch DVR Command |
CVE-2020-10514 |
|
Privilege Escalation |
iCatch DVR File Management Interface |
CVE-2020-10513 |
|
Privilege Escalation |
Intel Binary Configuration Tool Installer |
CVE-2020-0598 |
|
Privilege Escalation |
Intel Data Migration Software Permission |
CVE-2020-0547 |
|
Denial of Service |
Intel Driver and Support Assistant |
CVE-2020-0568 |
|
Memory Corruption |
Intel Modular Server MFS2600KISPP Compute Module |
CVE-2020-0576 |
|
unknown vulnerability |
Intel Modular Server MFS2600KISPP Compute Module |
CVE-2020-0577 |
|
Privilege Escalation |
Intel Modular Server MFS2600KISPP Compute Module |
CVE-2020-0578 |
|
Privilege Escalation |
Intel NUC |
CVE-2020-0600 |
|
Denial of Service |
Intel PROSet/Wireless WiFi Kernel Mode Driver |
CVE-2020-0558 |
|
Privilege Escalation |
Intel PROSet/Wireless WiFi Permission |
CVE-2020-0557 |
|
Information Disclosure |
Istio/Envoy |
CVE-2020-11767 |
|
Weak Authentication |
Jitsi Meet Default Credentials |
CVE-2020-11878 |
|
Denial of Service |
Juniper Junos BGP UPDATE |
CVE-2020-1632 |
|
Information Disclosure |
KDE KMail |
CVE-2020-11880 |
|
Privilege Escalation |
Lenovo System Interface Foundation LenovoAppScenarioPluginSystem |
CVE-2020-8324 |
|
Privilege Escalation |
Lenovo System Interface Foundation LenovoBatteryGaugePackage |
CVE-2020-8327 |
|
Privilege Escalation |
Lenovo System Interface Foundation LenovoSystemUpdatePlugin |
CVE-2020-8318 |
|
Privilege Escalation |
Lenovo System Interface Foundation |
CVE-2020-8319 |
|
Information Disclosure |
Lenovo Vantage |
CVE-2020-8316 |
|
Privilege Escalation |
LG Mobile Device Factory Reset Protection |
CVE-2020-11874 |
|
Memory Corruption |
LG Mobile Device Logging Tool Stack-based |
CVE-2020-11873 |
|
Privilege Escalation |
LG Mobile Device MTK Kernel |
CVE-2020-11875 |
|
Denial of Service |
libsixel loader.c load_png |
CVE-2020-11721 |
|
Denial of Service |
libssh AES-CTR/DES Crash |
CVE-2020-1730 |
|
Denial of Service |
libssh AES-CTR/DES Crash |
CVE-2020-1730 |
|
unknown vulnerability |
Linux Kernel control.c snd_ctl_elem_add |
CVE-2020-11725 |
|
unknown vulnerability |
Linux Kernel idle_book3s.S |
CVE-2020-11669 |
|
Information Disclosure |
Linux Kernel |
CVE-2020-8832 |
|
Remote Code Execution |
MB Connect Line mymbCONNECT24/mbCONNECT24 backup-scheduler |
CVE-2020-10382 |
|
Remote Code Execution |
MB Connect Line mymbCONNECT24/mbCONNECT24 com_mb24sysapi |
CVE-2020-10383 |
|
Privilege Escalation |
MB Connect Line mymbCONNECT24/mbCONNECT24 |
CVE-2020-10384 |
|
SQL Injection |
MB Connect Line mymbCONNECT24/mbCONNECT24 |
CVE-2020-10381 |
|
Privilege Escalation |
McAfee Endpoint Security Access Control |
CVE-2020-7278 |
|
Privilege Escalation |
McAfee Endpoint Security ACL |
CVE-2020-7273 |
|
Privilege Escalation |
McAfee Endpoint Security Local Security Protection |
CVE-2020-7259 |
|
Privilege Escalation |
McAfee Endpoint Security McTray.exe |
CVE-2020-7274 |
|
Memory Corruption |
McAfee Endpoint Security |
CVE-2020-7261 |
|
Privilege Escalation |
McAfee Endpoint Security Protection Mechanism |
CVE-2020-7277 |
|
Privilege Escalation |
McAfee Endpoint Security Symbolic Links |
CVE-2020-7250 |
|
Privilege Escalation |
McAfee Endpoint Security Symbolic Links |
CVE-2020-7257 |
|
Privilege Escalation |
McAfee Endpoint Security User Permission |
CVE-2020-7255 |
|
Weak Authentication |
McAfee Endpoint Security |
CVE-2020-7276 |
|
Privilege Escalation |
McAfee ndpoint Security Uninstaller |
CVE-2020-7275 |
|
Cross Site Scripting |
Media Library Assistant Plugin |
CVE-2020-11731 |
|
Privilege Escalation |
Media Library Assistant Plugin Local File Inclusion |
CVE-2020-11732 |
|
Privilege Escalation |
Micro Focus Enterprise Developer and Enterprise Server |
CVE-2020-9523 |
|
Privilege Escalation |
Microsoft AutoUpdate for Mac |
CVE-2020-0984 |
|
Cross Site Scripting |
Microsoft |
CVE-2020-0976 |
|
Privilege Escalation |
Microsoft Defender Antimalware Platform Hardlink |
CVE-2020-0835 |
|
Cross Site Scripting |
Microsoft Dynamics 365 |
CVE-2020-1049 |
|
Cross Site Scripting |
Microsoft Dynamics 365 |
CVE-2020-1050 |
|
Information Disclosure |
Microsoft Dynamics NAV |
CVE-2020-1018 |
|
Privilege Escalation |
Microsoft Dynamics NAV |
CVE-2020-1022 |
|
Memory Corruption |
Microsoft Edge/ChakraCore Chakra Scripting Engine |
CVE-2020-0969 |
|
Memory Corruption |
Microsoft Edge/ChakraCore Scripting Engine |
CVE-2020-0970 |
|
Directory Traversal |
Microsoft Forefront Endpoint Protection MpSigStub.exe |
CVE-2020-1002 |
|
Memory Corruption |
Microsoft Internet Explorer Scripting Engine |
CVE-2020-0968 |
|
Memory Corruption |
Microsoft Internet Explorer VBScript Engine |
CVE-2020-0895 |
|
Memory Corruption |
Microsoft Internet Explorer VBScript |
CVE-2020-0966 |
|
Memory Corruption |
Microsoft Internet Explorer VBScript |
CVE-2020-0967 |
|
Memory Corruption |
Microsoft Office 365 ProPlus Excel |
CVE-2020-0979 |
|
Memory Corruption |
Microsoft Office Access Connectivity Engine |
CVE-2020-0961 |
|
Memory Corruption |
Microsoft Office |
CVE-2020-0991 |
|
Privilege Escalation |
Microsoft Office |
CVE-2020-0760 |
|
Memory Corruption |
Microsoft Office/Excel/Office 365 |
CVE-2020-0906 |
|
Memory Corruption |
Microsoft Office/SharePoint/Word |
CVE-2020-0980 |
|
Privilege Escalation |
Microsoft OneDrive |
CVE-2020-0935 |
|
Privilege Escalation |
Microsoft Remote Desktop For Mac |
CVE-2020-0919 |
|
Information Disclosure |
Microsoft Research JavaScript Cryptography Library ECC |
CVE-2020-1026 |
|
Privilege Escalation |
Microsoft RMS Sharing for Mac |
CVE-2020-1019 |
|
Privilege Escalation |
Microsoft SharePoint Enterprise Server Application Package |
CVE-2020-0929 |
|
Privilege Escalation |
Microsoft SharePoint Enterprise Server Application Package |
CVE-2020-0929 |
|
Privilege Escalation |
Microsoft SharePoint Enterprise Server Application Package |
CVE-2020-0931 |
|
Privilege Escalation |
Microsoft SharePoint Enterprise Server Application Package |
CVE-2020-0931 |
|
Privilege Escalation |
Microsoft SharePoint Enterprise Server Application Package |
CVE-2020-0932 |
|
Privilege Escalation |
Microsoft SharePoint Enterprise Server Application Package |
CVE-2020-0932 |
|
Privilege Escalation |
Microsoft SharePoint Enterprise Server Application Package |
CVE-2020-0971 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0923 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0924 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0925 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0926 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0930 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0933 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0954 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0972 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0973 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0975 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0977 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server |
CVE-2020-0978 |
|
Privilege Escalation |
Microsoft SharePoint Enterprise Server Source Markup |
CVE-2020-0920 |
|
Privilege Escalation |
Microsoft SharePoint Enterprise Server/SharePoint Server Application Package |
CVE-2020-0974 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server/SharePoint Server |
CVE-2020-0927 |
|
Cross Site Scripting |
Microsoft SharePoint Enterprise Server/SharePoint Server |
CVE-2020-0927 |
|
Privilege Escalation |
Microsoft Visual Studio Extension Installer Service |
CVE-2020-0900 |
|
Privilege Escalation |
Microsoft Visual Studio Updater Service |
CVE-2020-0899 |
|
Privilege Escalation |
Microsoft WebEx Network Recording Player/Webex Player ARF |
CVE-2020-3194 |
|
Privilege Escalation |
Microsoft Windows Adobe Font Manager Library |
CVE-2020-0938 |
|
Privilege Escalation |
Microsoft Windows Adobe Font Manager Library |
CVE-2020-0938 |
|
Privilege Escalation |
Microsoft Windows Adobe Font Manager Library |
CVE-2020-0938 |
|
Privilege Escalation |
Microsoft Windows Adobe Font Manager Library |
CVE-2020-1020 |
|
Memory Corruption |
Microsoft Windows Codecs Library |
CVE-2020-0965 |
|
Memory Corruption |
Microsoft Windows Codecs Library |
CVE-2020-0965 |
|
Privilege Escalation |
Microsoft Windows Connected User Experiences and Telemetry Service |
CVE-2020-0942 |
|
Privilege Escalation |
Microsoft Windows Connected User Experiences and Telemetry Service |
CVE-2020-0944 |
|
Privilege Escalation |
Microsoft Windows Connected User Experiences and Telemetry Service |
CVE-2020-1029 |
|
Denial of Service |
Microsoft Windows |
CVE-2020-0794 |
|
Memory Corruption |
Microsoft Windows DirectX |
CVE-2020-0784 |
|
Memory Corruption |
Microsoft Windows DirectX |
CVE-2020-0888 |
|
Denial of Service |
Microsoft Windows DNS |
CVE-2020-0993 |
|
Information Disclosure |
Microsoft Windows GDI |
CVE-2020-0952 |
|
Memory Corruption |
Microsoft Windows GDI+ |
CVE-2020-0964 |
|
Information Disclosure |
Microsoft Windows Graphics Component |
CVE-2020-0982 |
|
Information Disclosure |
Microsoft Windows Graphics Component |
CVE-2020-0987 |
|
Information Disclosure |
Microsoft Windows Graphics Component |
CVE-2020-1005 |
|
unknown vulnerability |
Microsoft Windows Graphics Component |
CVE-2020-0907 |
|
Privilege Escalation |
Microsoft Windows Graphics Component |
CVE-2020-1004 |
|
Privilege Escalation |
Microsoft Windows Graphics |
CVE-2020-0687 |
|
Memory Corruption |
Microsoft Windows Hyper-V |
CVE-2020-0910 |
|
Memory Corruption |
Microsoft Windows Hyper-V |
CVE-2020-0917 |
|
Memory Corruption |
Microsoft Windows Hyper-V |
CVE-2020-0918 |
|
Information Disclosure |
Microsoft Windows |
CVE-2020-0821 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-0889 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-0953 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-0959 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-0960 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-0988 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-0992 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-0994 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-0995 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-0999 |
|
Memory Corruption |
Microsoft Windows JET Database Engine |
CVE-2020-1008 |
|
Information Disclosure |
Microsoft Windows Kernel |
CVE-2020-0955 |
|
Information Disclosure |
Microsoft Windows Kernel |
CVE-2020-1007 |
|
Memory Corruption |
Microsoft Windows Kernel |
CVE-2020-0913 |
|
Memory Corruption |
Microsoft Windows Kernel |
CVE-2020-1000 |
|
Memory Corruption |
Microsoft Windows Kernel |
CVE-2020-1003 |
|
Memory Corruption |
Microsoft Windows Kernel |
CVE-2020-1027 |
|
Information Disclosure |
Microsoft Windows Media Foundation |
CVE-2020-0937 |
|
Information Disclosure |
Microsoft Windows Media Foundation |
CVE-2020-0939 |
|
Information Disclosure |
Microsoft Windows Media Foundation |
CVE-2020-0945 |
|
Information Disclosure |
Microsoft Windows Media Foundation |
CVE-2020-0946 |
|
Information Disclosure |
Microsoft Windows Media Foundation |
CVE-2020-0947 |
|
Memory Corruption |
Microsoft Windows Media Foundation |
CVE-2020-0948 |
|
Memory Corruption |
Microsoft Windows Media Foundation |
CVE-2020-0948 |
|
Memory Corruption |
Microsoft Windows Media Foundation |
CVE-2020-0949 |
|
Memory Corruption |
Microsoft Windows Media Foundation |
CVE-2020-0949 |
|
Memory Corruption |
Microsoft Windows Media Foundation |
CVE-2020-0950 |
|
Memory Corruption |
Microsoft Windows Media Foundation |
CVE-2020-0950 |
|
Memory Corruption |
Microsoft Windows |
CVE-2020-0983 |
|
Memory Corruption |
Microsoft Windows Notification Service |
CVE-2020-0940 |
|
Memory Corruption |
Microsoft Windows Notification Service |
CVE-2020-1001 |
|
Information Disclosure |
Microsoft Windows Push Notification Service |
CVE-2020-1016 |
|
Memory Corruption |
Microsoft Windows Push Notification Service |
CVE-2020-1006 |
|
Memory Corruption |
Microsoft Windows Push Notification Service |
CVE-2020-1017 |
|
Privilege Escalation |
Microsoft Windows Scheduled Task |
CVE-2020-0936 |
|
Privilege Escalation |
Microsoft Windows Store Install Service |
CVE-2020-1009 |
|
Privilege Escalation |
Microsoft Windows System Assessment Tool |
CVE-2020-1011 |
|
Privilege Escalation |
Microsoft Windows Token Security Feature |
CVE-2020-0981 |
|
Privilege Escalation |
Microsoft Windows Update Client |
CVE-2020-1014 |
|
Memory Corruption |
Microsoft Windows Update Stack |
CVE-2020-0985 |
|
Memory Corruption |
Microsoft Windows Update Stack |
CVE-2020-0996 |
|
Memory Corruption |
Microsoft Windows User-Mode Power Service |
CVE-2020-1015 |
|
Information Disclosure |
Microsoft Windows Win32k |
CVE-2020-0699 |
|
Information Disclosure |
Microsoft Windows Win32k |
CVE-2020-0962 |
|
Memory Corruption |
Microsoft Windows Win32k |
CVE-2020-0956 |
|
Memory Corruption |
Microsoft Windows Win32k |
CVE-2020-0957 |
|
Memory Corruption |
Microsoft Windows Win32k |
CVE-2020-0958 |
|
Privilege Escalation |
Microsoft Windows Work Folder Service |
CVE-2020-1094 |
|
Memory Corruption |
Microsoft Windows WpcDesktopMonSvc |
CVE-2020-0934 |
|
Weak Authentication |
Microsoft YourPhone App |
CVE-2020-0943 |
|
Weak Encryption |
Mitel MiVoice Connect Client Credentials |
CVE-2020-10377 |
|
Remote Code Execution |
Mitel MiVoice Connect UCB |
CVE-2020-10211 |
|
Privilege Escalation |
Netgear FS728TLP Access Control |
CVE-2019-20676 |
|
Information Disclosure |
Netgear FS728TLP |
CVE-2019-20658 |
|
Cross Site Scripting |
Netgear JGS516PE Reflected |
CVE-2020-11791 |
|
Privilege Escalation |
Netgear MR1100 Access Control |
CVE-2019-20679 |
|
Information Disclosure |
Netgear MR1100 |
CVE-2019-20649 |
|
Command Injection |
Netgear R6400v2/R6700/R6700v3/R6900/R7900 |
CVE-2019-20659 |
|
Command Injection |
Netgear R6400v2/R6700/R6700v3/R6900/R7900 |
CVE-2020-11789 |
|
Weak Authentication |
Netgear R6900v2 |
CVE-2019-20681 |
|
Weak Authentication |
Netgear R6900v2 |
CVE-2020-11788 |
|
Remote Code Execution |
Netgear R7800 |
CVE-2020-11790 |
|
Information Disclosure |
Netgear R8900/R9000/RAX120/XR700 TLS Key |
CVE-2020-11792 |
|
Denial of Service |
Netgear R8900/R9000/XR500/XR700 |
CVE-2019-20650 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20660 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20664 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20665 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20667 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20668 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20669 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20671 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20673 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20674 |
|
Cross Site Scripting |
Netgear RBK50 Stored |
CVE-2019-20678 |
|
Cross Site Scripting |
Netgear RBR50/RBS50/RBK50 Stored |
CVE-2019-20661 |
|
Cross Site Scripting |
Netgear RBR50/RBS50/RBK50 Stored |
CVE-2019-20662 |
|
Cross Site Scripting |
Netgear RBR50/RBS50/RBK50 Stored |
CVE-2019-20663 |
|
Cross Site Scripting |
Netgear RBR50/RBS50/RBK50 Stored |
CVE-2019-20666 |
|
Cross Site Scripting |
Netgear RBR50/RBS50/RBK50 Stored |
CVE-2019-20670 |
|
Cross Site Scripting |
Netgear RBR50/RBS50/RBK50 Stored |
CVE-2019-20672 |
|
Cross Site Scripting |
Netgear RBR50/RBS50/RBK50 Stored |
CVE-2019-20675 |
|
Cross Site Scripting |
Netgear RBR50/RBS50/RBK50 Stored |
CVE-2019-20677 |
|
Information Disclosure |
Netgear WAC505 |
CVE-2019-20652 |
|
Command Injection |
Netgear WAC505/WAC510 |
CVE-2019-20651 |
|
Information Disclosure |
Netgear WAC505/WAC510 Configuration |
CVE-2019-20654 |
|
Denial of Service |
Netgear WAC505/WAC510 |
CVE-2019-20653 |
|
Memory Corruption |
Netgear WNR2000v5 Stack-based |
CVE-2019-20767 |
|
Weak Authentication |
Netgear WNR2020 Default Credentials |
CVE-2019-20656 |
|
Memory Corruption |
Netgear WNR2020 |
CVE-2019-20657 |
|
Command Injection |
Netgear XR500 |
CVE-2019-20680 |
|
Command Injection |
Netgear XR500 |
CVE-2020-11770 |
|
Command Injection |
Netgear XR500/XR700 |
CVE-2019-20655 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11768 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11769 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11771 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11772 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11773 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11774 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11775 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11776 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11777 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11778 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11779 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11780 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11781 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11782 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11783 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11784 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11785 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11786 |
|
Cross Site Scripting |
Netgear XR700 Stored |
CVE-2020-11787 |
|
Cross Site Scripting |
Octech Oempro Campaign.Create |
CVE-2020-9460 |
|
Cross Site Scripting |
Octech Oempro Media.CreateFolder |
CVE-2020-9461 |
|
Privilege Escalation |
OnePlus 7 Pro Trusted Execution Environment |
CVE-2020-7958 |
|
Privilege Escalation |
ONLYOFFICE Document Server libxcb.so.1 |
CVE-2020-11535 |
|
Privilege Escalation |
ONLYOFFICE Document Server NSFileDownloader |
CVE-2020-11534 |
|
Privilege Escalation |
ONLYOFFICE Document Server unzip |
CVE-2020-11536 |
|
SQL Injection |
ONLYOFFICE Document Server WebSocket API |
CVE-2020-11537 |
|
Cross Site Scripting |
Open Upload |
CVE-2020-11712 |
|
Memory Corruption |
OpenEXR Compression ImfDwaCompressor.cpp uncompress |
CVE-2020-11762 |
|
Memory Corruption |
OpenEXR handleDeepFrameBuffer/readSampleCountForLineBlock |
CVE-2020-11759 |
|
Information Disclosure |
OpenEXR Huffman Uncompression ImfFastHuf.cpp refill |
CVE-2020-11761 |
|
Memory Corruption |
OpenEXR ImfMisc.cpp copyIntoFrameBuffer |
CVE-2020-11764 |
|
Memory Corruption |
OpenEXR ImfOptimizedPixelReading.h |
CVE-2020-11758 |
|
Memory Corruption |
OpenEXR ImfTileOffsets.cpp vector |
CVE-2020-11763 |
|
Information Disclosure |
OpenEXR ImfXdr.h Classifier |
CVE-2020-11765 |
|
Memory Corruption |
OpenEXR RLE Compression ImfRle.cpp rleUncompress |
CVE-2020-11760 |
|
Cross Site Scripting |
OpenMRS ActiveVisit Page |
CVE-2020-5731 |
|
Information Disclosure |
OpenMRS Data Exchange Module |
CVE-2020-5733 |
|
Privilege Escalation |
OpenMRS Data Exchange Module |
CVE-2020-5732 |
|
Cross Site Scripting |
OpenMRS Login Page |
CVE-2020-5730 |
|
Cross Site Scripting |
OpenMRS login.htm |
CVE-2020-5728 |
|
Cross Site Scripting |
OpenMRS UI Framework Error Page Reflected |
CVE-2020-5729 |
|
Privilege Escalation |
OpenNMS Horizon/Meridian HQL nodeList.htm addCriteriaForSnmpParm |
CVE-2020-11886 |
|
Privilege Escalation |
OpenResty API ngx_http_lua_subrequest.c |
CVE-2020-11724 |
|
unknown vulnerability |
OpenTrace Cloud Functions Subsystem |
CVE-2020-11872 |
|
Privilege Escalation |
Oracle WebLogic Server |
CVE-2020-2963 |
|
cross site request forgery |
ProVide Admin Interface |
CVE-2020-11706 |
|
Cross Site Scripting |
ProVide Admin Web Interface Reflected |
CVE-2020-11704 |
|
Privilege Escalation |
ProVide GetInheritedProperties |
CVE-2020-11703 |
|
Privilege Escalation |
ProVide ImportCertificate |
CVE-2020-11705 |
|
Privilege Escalation |
ProVide Permission Symlink |
CVE-2020-11707 |
|
Privilege Escalation |
ProVide SetUserInfo EXECUTE() |
CVE-2020-11708 |
|
cross site request forgery |
ProVide Web Interface |
CVE-2020-11701 |
|
Cross Site Scripting |
ProVide Web Interface Reflected |
CVE-2020-11702 |
|
Privilege Escalation |
Red Hat Ceph Storage/Openshift Container Storage Secure Mode Reuse |
CVE-2020-1759 |
|
Privilege Escalation |
SAP Business Client Integrity Check |
CVE-2020-6228 |
|
Information Disclosure |
SAP Business Intelligence Platform Admin Tools/Query Builder |
CVE-2020-6218 |
|
Cross Site Scripting |
SAP Business Intelligence Platform |
CVE-2020-6222 |
|
Cross Site Scripting |
SAP Business Intelligence Platform |
CVE-2020-6226 |
|
Cross Site Scripting |
SAP Business Intelligence Platform |
CVE-2020-6231 |
|
Privilege Escalation |
SAP Business Intelligence Platform Deserialization |
CVE-2020-6219 |
|
Information Disclosure |
SAP Business Intelligence Platform dswsbobje Web Application |
CVE-2020-6237 |
|
spoofing |
SAP Business Intelligence Platform Error Page spoofing |
CVE-2020-6223 |
|
Privilege Escalation |
SAP Business Intelligence Platform GIOP Packet |
CVE-2020-6227 |
|
Open Redirect |
SAP Business Intelligence Platform |
CVE-2020-6211 |
|
Information Disclosure |
SAP Business Intelligence Platform Password |
CVE-2020-6195 |
|
Cross Site Scripting |
SAP Business Intelligence Platform Reflected |
CVE-2020-6216 |
|
Cross Site Scripting |
SAP Business Intelligence Platform Web Intelligence HTML Interface |
CVE-2020-6221 |
|
Information Disclosure |
SAP Commerce |
CVE-2020-6232 |
|
Privilege Escalation |
SAP Commerce REST API |
CVE-2020-6238 |
|
Privilege Escalation |
SAP Host Agent |
CVE-2020-6234 |
|
Directory Traversal |
SAP Knowledge Management File API |
CVE-2020-6225 |
|
Privilege Escalation |
SAP Landscape Management/Adaptive Extensions |
CVE-2020-6236 |
|
Cross Site Scripting |
SAP NetWeaver AS ABAP Reflected |
CVE-2020-6229 |
|
Information Disclosure |
SAP NetWeaver AS JAVA HTTP Service |
CVE-2020-6224 |
|
Open Redirect |
SAP |
CVE-2020-6215 |
|
Privilege Escalation |
SAP OrientDB Code Injection |
CVE-2020-6230 |
|
Cross Site Scripting |
SAP Reflected |
CVE-2020-6217 |
|
Denial of Service |
SAP S-4HANA Banking Services |
CVE-2020-6233 |
|
Privilege Escalation |
SAP S-4HANA Report |
CVE-2020-6214 |
|
Weak Authentication |
SAP Solution Manager Diagnostics Agent |
CVE-2020-6235 |
|
Denial of Service |
Siemens KTK ATE530S Interniche-based TCP Stack |
CVE-2019-19300 |
|
Denial of Service |
Siemens SCALANCE X-200 VxWorks-based Profinet TCP Stack |
CVE-2019-19301 |
|
Privilege Escalation |
Sierra Wireless Windows Mobile Broadband Driver Package |
CVE-2020-8948 |
|
Directory Traversal |
Snap Creek Duplicator duplicator_init |
CVE-2020-11738 |
|
Privilege Escalation |
snap-core18 pc-kernel Snap Build Process |
CVE-2019-11480 |
|
Privilege Escalation |
Sophos Central Endpoint/Home Endpoint |
CVE-2020-10947 |
|
Denial of Service |
Synergy Systems & Solutions HUSKY RTU 6049-E70 |
CVE-2020-7800 |
|
Information Disclosure |
Synergy Systems & Solutions HUSKY RTU 6049-E70 |
CVE-2020-7801 |
|
Information Disclosure |
Synergy Systems & Solutions HUSKY RTU 6049-E70 SNMP |
CVE-2020-7802 |
|
Weak Authentication |
Synergy Systems & Solutions HUSKY RTU 6049-E70 Telnet Service |
CVE-2019-16879 |
|
Information Disclosure |
Triangle MicroWorks SCADA Data Gateway |
CVE-2020-10613 |
|
Denial of Service |
Triangle MicroWorks SCADA Data Gateway Stack-based |
CVE-2020-10615 |
|
Memory Corruption |
Triangle MicroWorks SCADA Data Gateway Type Confusion |
CVE-2020-10611 |
|
Memory Corruption |
Triangle MicroWorks Stack-based |
CVE-2020-6996 |
|
Privilege Escalation |
UniFi Cloud Key |
CVE-2020-8148 |
|
Information Disclosure |
VMware Tanzu Application Service for VMs Log Credentials |
CVE-2020-5406 |
|
Privilege Escalation |
VMware vCenter Server vmdir |
CVE-2020-3952 |
|
Cross Site Scripting |
VMware vRealize Log Insight |
CVE-2020-3953 |
|
Open Redirect |
VMware vRealize Log Insight |
CVE-2020-3954 |
|
Weak Encryption |
WindowsHello Open Source Library |
CVE-2020-11005 |
|
Denial of Service |
Wireshark BACapp Dissector packet-bacapp.c |
CVE-2020-11647 |
|
Denial of Service |
Xen Crash |
CVE-2020-11743 |
|
Denial of Service |
Xen GNTTABOP_copy |
CVE-2020-11742 |
|
Privilege Escalation |
Xen |
CVE-2020-11739 |
|
Information Disclosure |
Xen xenoprof |
CVE-2020-11740 |
|
Privilege Escalation |
Xen xenoprof |
CVE-2020-11741 |
|
Privilege Escalation |
Zoom Call Recording rs |
CVE-2019-18822 |
|
Weak Encryption |
Zoom Client for Meetings airhost.exe |
CVE-2020-11877 |
|
Weak Encryption |
Zoom Client for Meetings OpenSSL airhost.exe |
CVE-2020-11876 |