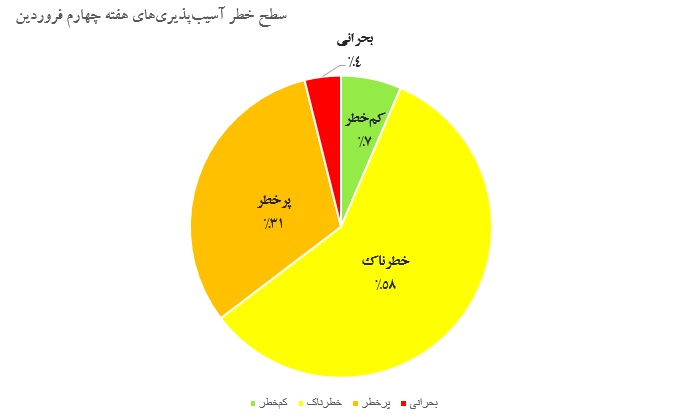
آسیبپذیریهای حیاتی هفته چهارم فروردینماه

این هفته در محصولات مهم Juniper و IBM چندین آسیبپذیری با سطح خطر «حیاتی» و «بالا» شناسایی شد. همچنین محصولات پرکاربرد شرکتهای Avira و Fortinet، کرنل لینوکس و SuSE نیز چندین آسیبپذیری حیاتی داشتند. امّا بیشترین آسیبپذیریهای این هفته مربوط به تجهیزات موبایل سامسونگ است که انواع آسیبپذیریها از ارتقاء امتیاز تا افشای اطلاعات را شامل میشود.
|
نوع آسیبپذیری |
محصول آسیبپذیر |
شناسه آسیبپذیر |
|
Directory Traversal |
Advantech WebAccess/NMS |
CVE-2020-10631 |
|
Directory Traversal |
Advantech WebAccess/NMS |
CVE-2020-10619 |
|
Privilege Escalation |
Advantech WebAccess/NMS File Upload |
CVE-2020-10621 |
|
Privilege Escalation |
Advantech WebAccess/NMS OS |
CVE-2020-10603 |
|
Privilege Escalation |
Advantech WebAccess/NMS |
CVE-2020-10625 |
|
SQL Injection |
Advantech WebAccess/NMS |
CVE-2020-10623 |
|
SQL Injection |
Advantech WebAccess/NMS |
CVE-2020-10617 |
|
Directory Traversal |
Advantech WebAccess/NMS XML Data |
CVE-2020-10629 |
|
Denial of Service |
Amcrest Camera/NVR Service Port 37777 NULL Pointer Dereference |
CVE-2020-5736 |
|
Memory Corruption |
Amcrest Camera/NVR Service Port 37777 Stack-based |
CVE-2020-5735 |
|
Command Injection |
apiconnect-cli-plugins |
CVE-2020-7633 |
|
Information Disclosure |
auth0.js Password |
CVE-2020-5263 |
|
Privilege Escalation |
Avira Free Anti-Virus Self-Protection Feature |
CVE-2020-8961 |
|
Cross Site Request Forgery |
Broadcom ProxySG/ASG Management Center |
CVE-2019-18376 |
|
Weak Authentication |
Broadcom ProxySG/ASG Management Interface Session Hijacking |
CVE-2019-18375 |
|
Information Disclosure |
Castle Rock SNMPc Online Backup File Credentials |
CVE-2020-11555 |
|
Information Disclosure |
Castle Rock SNMPc Online Cookie Credentials |
CVE-2020-11557 |
|
Cross Site Request Forgery |
Castle Rock SNMPc Online |
CVE-2020-11553 |
|
Information Disclosure |
Castle Rock SNMPc Online info.php4 |
CVE-2020-11554 |
|
Cross Site Scripting |
Castle Rock SNMPc Online Stored |
CVE-2020-11556 |
|
Remote Code Execution |
Centreon Infrastructure Monitoring Software |
CVE-2019-19699 |
|
Information Disclosure |
CIPPlanner CIPAce API |
CVE-2020-11592 |
|
Information Disclosure |
CIPPlanner CIPAce API |
CVE-2020-11591 |
|
Information Disclosure |
CIPPlanner CIPAce API Path |
CVE-2020-11595 |
|
Information Disclosure |
CIPPlanner CIPAce API Path |
CVE-2020-11594 |
|
Directory Traversal |
CIPPlanner CIPAce |
CVE-2020-11596 |
|
Information Disclosure |
CIPPlanner CIPAce ETL Process |
CVE-2020-11587 |
|
Information Disclosure |
CIPPlanner CIPAce GetDistributedPOP3 |
CVE-2020-11599 |
|
Information Disclosure |
CIPPlanner CIPAce HealthPage.aspx |
CVE-2020-11590 |
|
Information Disclosure |
CIPPlanner CIPAce |
CVE-2020-11593 |
|
Information Disclosure |
CIPPlanner CIPAce |
CVE-2020-11589 |
|
Information Disclosure |
CIPPlanner CIPAce |
CVE-2020-11588 |
|
SQL Injection |
CIPPlanner CIPAce |
CVE-2020-11597 |
|
Remote Code Execution |
CIPPlanner CIPAce Upload.ashx |
CVE-2020-11598 |
|
XML External Entity |
CIPPlanner CIPAce XML Data |
CVE-2020-11586 |
|
Command Injection |
ClamAV clamscan _is_clamav_binary |
CVE-2020-7613 |
|
Command Injection |
compass-compile |
CVE-2020-7635 |
|
Memory Corruption |
Dahua Products DDNS Test Command |
CVE-2020-9499 |
|
Denial of Service |
Dahua Products |
CVE-2020-9500 |
|
Cross Site Request Forgery |
EasyBlocks IPv6 |
CVE-2020-5549 |
|
Weak Authentication |
EasyBlocks IPv6 Management Console Session Fixation |
CVE-2020-5550 |
|
Privilege Escalation |
Eclipse Che Workspace Pod |
CVE-2020-10689 |
|
Cross Site Request Forgery |
EJBCA CA UI |
CVE-2020-11627 |
|
Remote Code Execution |
EJBCA CA UI |
CVE-2020-11631 |
|
Privilege Escalation |
EJBCA Configuration |
CVE-2020-11628 |
|
Cross Site Scripting |
EJBCA |
CVE-2020-11626 |
|
Privilege Escalation |
EJBCA External Command Certificate Validator |
CVE-2020-11629 |
|
Privilege Escalation |
EJBCA Peer Protocol Deserialization |
CVE-2020-11630 |
|
Memory Corruption |
Facebook Instagram App Image Upload Heap-based |
CVE-2020-1895 |
|
unknown vulnerability |
FasterXML jackson-databind org.apache.commons.jelly.impl.Embedded |
CVE-2020-11620 |
|
unknown vulnerability |
FasterXML jackson-databind |
CVE-2020-11619 |
|
Cross Site Scripting |
Fortinet FortiADC Dashboard |
CVE-2020-6647 |
|
Privilege Escalation |
Fortinet FortiADC |
CVE-2020-9286 |
|
Denial of Service |
Fortinet FortiSwitch/FortiAnalyzer/FortiManager Admin WebUI |
CVE-2019-17657 |
|
Weak Authentication |
GE Mark VIe Controller Application Default Admin Password |
CVE-2019-13559 |
|
Weak Authentication |
GE Mark VIe Controller Telnet Server Default Credentials |
CVE-2019-13554 |
|
Privilege Escalation |
GitHub Community Edition/Enterprise Edition Pipeline |
CVE-2020-10981 |
|
Server-Side Request Forgery |
GitLab Community Edition/Enterprise Edition FogBugz |
CVE-2020-10980 |
|
Information Disclosure |
GitLab Community Edition/Enterprise Edition |
CVE-2020-10979 |
|
Information Disclosure |
GitLab Community Edition/Enterprise Edition |
CVE-2020-10976 |
|
Directory Traversal |
GitLab Community Edition/Enterprise Edition Project |
CVE-2020-10977 |
|
Information Disclosure |
GitLab Community Edition/Enterprise Edition Vulnerability Feedback Page |
CVE-2020-10975 |
|
Information Disclosure |
GitLab Community Edition/Enterprise Edition Web UI/GraphQL API |
CVE-2020-10978 |
|
Privilege Escalation |
HCL AppScan Authorization |
CVE-2019-4393 |
|
XML External Entity |
HCL AppScan XML Data |
CVE-2019-4391 |
|
Information Disclosure |
Huawei Mate 30/Mate 30 Pro |
CVE-2020-1801 |
|
Privilege Escalation |
Huawei OSCA-550/OSCA-550A/OSCA-550AX/OSCA-550X |
CVE-2020-1802 |
|
Cross Site Scripting |
IBM DOORS Next Generation Web UI |
CVE-2020-4252 |
|
Cross Site Scripting |
IBM DOORS Next Generation Web UI |
CVE-2019-4746 |
|
Cross Site Scripting |
IBM DOORS Next Generation Web UI |
CVE-2019-4740 |
|
Cross Site Scripting |
IBM DOORS Next Generation Web UI |
CVE-2019-4737 |
|
Privilege Escalation |
IBM Quality Manager REST API |
CVE-2019-4603 |
|
Information Disclosure |
IBM Quality Manager Trace |
CVE-2019-4601 |
|
Cross Site Scripting |
IBM Quality Manager Web UI |
CVE-2019-4602 |
|
Privilege Escalation |
IBM Security Information Queue Configuration |
CVE-2020-4290 |
|
Information Disclosure |
IBM Security Information Queue Error |
CVE-2020-4164 |
|
Information Disclosure |
IBM Security Information Queue httponly |
CVE-2020-4289 |
|
Privilege Escalation |
IBM Security Information Queue |
CVE-2020-4282 |
|
Information Disclosure |
IBM Security Information Queue Web UI |
CVE-2020-4291 |
|
Information Disclosure |
IBM Security Information Queue Web UI |
CVE-2020-4284 |
|
Privilege Escalation |
IBM Spectrum Scale |
CVE-2020-4273 |
|
Privilege Escalation |
IBM WebSphere Application Server SOAP Connector |
CVE-2020-4362 |
|
Cross Site Scripting |
IMPress for IDX Broker Plugin Stored |
CVE-2020-11512 |
|
Privilege Escalation |
IMPress for IDX Broker Plugin wrappers.php |
CVE-2020-9514 |
|
Weak Authentication |
Juniper JATP/vJATP SSH Service |
CVE-2020-1616 |
|
Denial of Service |
Juniper Junos BGP FlowSpec |
CVE-2020-1613 |
|
Information Disclosure |
Juniper Junos configd Streamer Log Hash |
CVE-2020-1620 |
|
Information Disclosure |
Juniper Junos configd Trace Hash |
CVE-2020-1621 |
|
Denial of Service |
Juniper Junos Configuration |
CVE-2020-1634 |
|
Information Disclosure |
Juniper Junos Configuration File Hash |
CVE-2020-1624 |
|
Information Disclosure |
Juniper Junos Configuration File |
CVE-2020-1623 |
|
Weak Authentication |
Juniper Junos Console Port |
CVE-2020-1618 |
|
Denial of Service |
Juniper Junos Crash |
CVE-2020-1627 |
|
Weak Authentication |
Juniper Junos Default Credentials |
CVE-2020-1615 |
|
Denial of Service |
Juniper Junos |
CVE-2020-1617 |
|
Denial of Service |
Juniper Junos Ethernet OAM |
CVE-2020-1639 |
|
Information Disclosure |
Juniper Junos EvoSharedObjStore Hash |
CVE-2020-1622 |
|
Denial of Service |
Juniper Junos Flooding |
CVE-2020-1626 |
|
Denial of Service |
Juniper Junos FPC Crash |
CVE-2020-1638 |
|
Information Disclosure |
Juniper Junos |
CVE-2020-1628 |
|
Denial of Service |
Juniper Junos IRB Memory Leak |
CVE-2020-1625 |
|
Denial of Service |
Juniper Junos NDP Proxy |
CVE-2020-1633 |
|
Privilege Escalation |
Juniper Junos Next-Generation Routing Engine |
CVE-2020-1619 |
|
Privilege Escalation |
Juniper Junos Routing Engine |
CVE-2020-1630 |
|
Denial of Service |
Juniper Junos RPD Crash |
CVE-2020-1629 |
|
Privilege Escalation |
Juniper Junos UAC Policy |
CVE-2020-1637 |
|
Weak Authentication |
Juniper NFX250 Default Credentials |
CVE-2020-1614 |
|
Privilege Escalation |
KeyCloak Admin Console Clickjacking |
CVE-2020-1728 |
|
unknown vulnerability |
Linux Kernel idle_book3s.S |
CVE-2020-11669 |
|
Information Disclosure |
Linux Kernel |
CVE-2020-8832 |
|
Memory Corruption |
Linux Kernel Keycode Table input.c input_set_keycode |
CVE-2019-20636 |
|
Information Disclosure |
Linux Kernel KVM Hypervisor |
CVE-2020-2732 |
|
Denial of Service |
Linux Kernel KVM kvmppc_restore_tm()") |
CVE-2020-8834 |
|
Memory Corruption |
Linux Kernel mempolicy.c mpol_parse_str |
CVE-2020-11565 |
|
Denial of Service |
Linux Kernel ov519.c ov518_mode_init_regs |
CVE-2020-11608 |
|
Denial of Service |
Linux Kernel stv06xx Subsystem stv06xx.c |
CVE-2020-11609 |
|
unknown vulnerability |
Linux Kernel Xirlink Camera USB Driver xirlink_cit.c |
CVE-2020-11668 |
|
Directory Traversal |
LogicalDOC servlet.gupld |
CVE-2020-10366 |
|
Code Execution |
Malwarebytes AdwCleaner DLL |
CVE-2020-11507 |
|
Privilege Escalation |
MicroK8s Provisioning |
CVE-2019-15789 |
|
Weak Authentication |
MongoDB Enterprise Kubernetes Operator X.509 Certificate Generator |
CVE-2020-7922 |
|
Privilege Escalation |
NCH Express Invoice Add New Item Screen |
CVE-2020-11561 |
|
Information Disclosure |
NCH Express Invoice Configuration File Cleartext |
CVE-2020-11560 |
|
Command Injection |
node-mpv |
CVE-2020-7632 |
|
Privilege Escalation |
OneTone Theme Options theme-functions.php |
CVE-2019-17230 |
|
Cross Site Scripting |
OneTone Theme theme-functions.php |
CVE-2019-17231 |
|
Weak Authentication |
OpsRamp Gateway SSH Service Backdoor |
CVE-2020-11543 |
|
Privilege Escalation |
Palo Alto Global Protect Agent |
CVE-2020-1989 |
|
Privilege Escalation |
Palo Alto Global Protect Agent Unquoted Search Path |
CVE-2020-1988 |
|
Information Disclosure |
Palo Alto Networks Global Protect Agent Logging |
CVE-2020-1987 |
|
|
Palo Alto PAN-OS Log Forwarding Card Format String |
CVE-2020-1992 |
|
Memory Corruption |
Palo Alto PAN-OS Management Server Stack-based |
CVE-2020-1990 |
|
Privilege Escalation |
Palo Alto Traps Temp File |
CVE-2020-1991 |
|
Weak Authentication |
Palo Alto VM Series Firewall for Microsoft Azure TechSupport Files |
CVE-2020-1978 |
|
Privilege Escalation |
Pulse Secure Pulse Connect Secure Applet tncc.jar |
CVE-2020-11582 |
|
Privilege Escalation |
Pulse Secure Pulse Connect Secure Applet tncc.jar Runtime.getRuntime().exec() |
CVE-2020-11581 |
|
Weak Authentication |
Pulse Secure Pulse Connect Secure Applet tncc.jar |
CVE-2020-11580 |
|
Memory Corruption |
QEMU tulip.c |
CVE-2020-11102 |
|
Privilege Escalation |
QQBrowser Windows Service TsService.exe |
CVE-2020-10551 |
|
Cross Site Request Forgery |
Revive Adserver CSRF Protection |
CVE-2020-8143 |
|
Privilege Escalation |
Revive Adserver User Interface |
CVE-2020-8142 |
|
Memory Corruption |
Samsung Mobile Devices Bootloader Integer Overflow |
CVE-2018-21089 |
|
Remote Code Execution |
Samsung Mobile Devices Call+ App |
CVE-2018-21075 |
|
Privilege Escalation |
Samsung Mobile Devices Charger |
CVE-2018-21061 |
|
Information Disclosure |
Samsung Mobile Devices Clipboard |
CVE-2018-21077 |
|
Information Disclosure |
Samsung Mobile Devices Clipboard |
CVE-2018-21059 |
|
Weak Authentication |
Samsung Mobile Devices Clipboard |
CVE-2018-21073 |
|
Privilege Escalation |
Samsung Mobile Devices Contacts App |
CVE-2018-21078 |
|
Information Disclosure |
Samsung Mobile Devices Debug Log |
CVE-2018-21074 |
|
Privilege Escalation |
Samsung Mobile Devices DeviceTest Application |
CVE-2018-21092 |
|
Weak Authentication |
Samsung Mobile Devices Dex Station |
CVE-2018-21082 |
|
Memory Corruption |
Samsung Mobile Devices Driver Input Booster |
CVE-2018-21064 |
|
Privilege Escalation |
Samsung Mobile Devices Dual Messenger |
CVE-2018-21081 |
|
Remote Code Execution |
Samsung Mobile Devices Dual Messenger |
CVE-2018-21042 |
|
Memory Corruption |
Samsung Mobile Devices eCryptFS Integer Underflow |
CVE-2018-21065 |
|
Memory Corruption |
Samsung Mobile Devices eCryptFS Integer Underflow |
CVE-2018-21054 |
|
Information Disclosure |
Samsung Mobile Devices Edge Lighting |
CVE-2020-11607 |
|
Information Disclosure |
Samsung Mobile Devices Emergency Dialer |
CVE-2018-21046 |
|
Memory Corruption |
Samsung Mobile Devices esecomm Trustlet Code Execution |
CVE-2018-21050 |
|
Memory Corruption |
Samsung Mobile Devices Exynos Modem Chipset |
CVE-2018-21090 |
|
Privilege Escalation |
Samsung Mobile Devices Factory Reset Protection |
CVE-2018-21047 |
|
Memory Corruption |
Samsung Mobile Devices Fingerprint Trustlet Code Execution |
CVE-2020-11600 |
|
Memory Corruption |
Samsung Mobile Devices Fingerprint Trustlet Code Execution |
CVE-2018-21051 |
|
Memory Corruption |
Samsung Mobile Devices g2d Driver Use-After-Free |
CVE-2018-21040 |
|
Information Disclosure |
Samsung Mobile Devices g2d_drv Driver |
CVE-2018-21043 |
|
Memory Corruption |
Samsung Mobile Devices get_kek Use-After-Free |
CVE-2018-21084 |
|
Information Disclosure |
Samsung Mobile Devices Google Assistant |
CVE-2020-11602 |
|
Memory Corruption |
Samsung Mobile Devices Kernel Driver Out-of-Bounds |
CVE-2018-21072 |
|
Information Disclosure |
Samsung Mobile Devices Keyboard |
CVE-2018-21060 |
|
Privilege Escalation |
Samsung Mobile Devices Keymaster AES-GCM Cache |
CVE-2018-21058 |
|
Privilege Escalation |
Samsung Mobile Devices Keymaster |
CVE-2018-21063 |
|
Privilege Escalation |
Samsung Mobile Devices Lockscreen |
CVE-2018-21053 |
|
Privilege Escalation |
Samsung Mobile Devices Lockscreen |
CVE-2018-21045 |
|
Information Disclosure |
Samsung Mobile Devices MediaTek Driver Memory |
CVE-2018-21069 |
|
Memory Corruption |
Samsung Mobile Devices MLDAP Trustlet Out-of-Bounds |
CVE-2020-11604 |
|
Memory Corruption |
Samsung Mobile Devices MLDAP Trustlet Type Confusion |
CVE-2020-11603 |
|
Information Disclosure |
Samsung Mobile Devices NFC Log |
CVE-2020-11605 |
|
Privilege Escalation |
Samsung Mobile Devices NFC |
CVE-2018-21080 |
|
Privilege Escalation |
Samsung Mobile Devices |
CVE-2018-21071 |
|
Privilege Escalation |
Samsung Mobile Devices |
CVE-2018-21055 |
|
Weak Authentication |
Samsung Mobile Devices Quick Tools Lockscreen |
CVE-2018-21039 |
|
Privilege Escalation |
Samsung Mobile Devices Secure Boot |
CVE-2018-21070 |
|
Information Disclosure |
Samsung Mobile Devices Secure Driver |
CVE-2018-21076 |
|
Privilege Escalation |
Samsung Mobile Devices Secure Folder App |
CVE-2018-21041 |
|
Weak Authentication |
Samsung Mobile Devices Secure Folder App |
CVE-2018-21038 |
|
Information Disclosure |
Samsung Mobile Devices Secure Folder |
CVE-2020-11606 |
|
Information Disclosure |
Samsung Mobile Devices Secure Folder |
CVE-2018-21062 |
|
Information Disclosure |
Samsung Mobile Devices Secure Folder Notification |
CVE-2018-21056 |
|
Privilege Escalation |
Samsung Mobile Devices Secure Folder |
CVE-2020-11601 |
|
Weak Authentication |
Samsung Mobile Devices Secure Folder |
CVE-2018-21068 |
|
Memory Corruption |
Samsung Mobile Devices SEM Trustlet Code Execution |
CVE-2018-21044 |
|
Memory Corruption |
Samsung Mobile Devices Shannon Baseband Stack-based |
CVE-2018-21057 |
|
Information Disclosure |
Samsung Mobile Devices Standalone Dex Mode |
CVE-2018-21048 |
|
Denial of Service |
Samsung Mobile Devices System Service Reboot |
CVE-2018-21088 |
|
Denial of Service |
Samsung Mobile Devices Telecom Crash |
CVE-2018-21091 |
|
Information Disclosure |
Samsung Mobile Devices Trustlet |
CVE-2018-21067 |
|
Memory Corruption |
Samsung Mobile Devices Trustlet |
CVE-2018-21066 |
|
Memory Corruption |
Samsung Mobile Devices Trustlet |
CVE-2018-21049 |
|
Information Disclosure |
Samsung Mobile Devices trustonic_tee |
CVE-2018-21083 |
|
Information Disclosure |
Samsung Mobile Devices USB Gadget Driver |
CVE-2018-21079 |
|
Memory Corruption |
Samsung Mobile Devices vaultkeeper Trustlet |
CVE-2018-21052 |
|
Memory Corruption |
Samsung Mobile Devices vnswap store |
CVE-2018-21087 |
|
Memory Corruption |
Samsung Mobile Devices vnswap_deinit_backing_storage Use-After-Free |
CVE-2018-21085 |
|
Memory Corruption |
Samsung Mobile Devices vnswap_init_backing_storage Double-Free |
CVE-2018-21086 |
|
Privilege Escalation |
sds set.js set |
CVE-2020-7618 |
|
Denial of Service |
Secdo Crash |
CVE-2020-1986 |
|
Privilege Escalation |
Secdo Permission Logs |
CVE-2020-1985 |
|
Privilege Escalation |
Secdo Privileges |
CVE-2020-1984 |
|
Memory Corruption |
SQLite ALTER TABLE Statement Use-After-Free |
CVE-2020-11656 |
|
Denial of Service |
SQLite Window-Function Query Segmentation Fault |
CVE-2020-11655 |
|
Privilege Escalation |
STMicroelectronics STM32F1 Access Control |
CVE-2020-8004 |
|
Privilege Escalation |
SuSE Linux Enterprise Server autoyast2 |
CVE-2019-18905 |
|
Denial of Service |
SuSE Linux Enterprise Server Resource Exhaustion |
CVE-2019-18904 |
|
Privilege Escalation |
SuSE Openstack Cloud/OpenStack Cloud Crowbar |
CVE-2018-17954 |
|
Privilege Escalation |
Symantec Data Center Security Manager |
CVE-2020-5832 |
|
SQL Injection |
TestLink dragdroptreenodes.php |
CVE-2020-8637 |
|
Privilege Escalation |
TestLink File Upload keywordsImport.php |
CVE-2020-8639 |
|
SQL Injection |
TestLink planUrgency.php |
CVE-2020-8638 |
|
Remote Code Execution |
utils-extend |
CVE-2020-8147 |
|
Memory Corruption |
VISAM VBASE Editor/VBASE Web-Remote Module ActiveX |
CVE-2020-10599 |
|
Information Disclosure |
VISAM VBASE Editor/VBASE Web-Remote Module Key |
CVE-2020-7000 |
|
weak encryption |
VISAM VBASE Editor/VBASE Web-Remote Module Password Hash |
CVE-2020-10601 |
|
Privilege Escalation |
VISAM VBASE Editor/VBASE Web-Remote Module |
CVE-2020-7004 |
|
Information Disclosure |
VISAM VBASE Editor/VBASE Web-Remote Module URL |
CVE-2020-7008 |
|
Privilege Escalation |
VMware vCenter Server vmdir |
CVE-2020-3952 |
|
Cross Site Scripting |
WP Lead Plus X Plugin c37_wpl_import_template |
CVE-2020-11509 |
|
Cross Site Scripting |
WP Lead Plus X Plugin wp_ajax_core37_lp_save_page |
CVE-2020-11508 |
|
Privilege Escalation |
xdLocalStorage xdLocalStorage.js buildMessage() |
CVE-2020-11611 |
|
Information Disclosure |
xdLocalStorage xdLocalStoragePostMessageApi.js postData() |
CVE-2020-11610 |
|
Privilege Escalation |
Xiaomi XIAOAI speaker Pro LX06 Failsafe Mode |
CVE-2020-10262 |
|
Privilege Escalation |
Xiaomi XIAOAI speaker Pro LX06 UART Interface |
CVE-2020-10263 |
|
weak encryption |
Zoom Client for Meetings |
CVE-2020-11500 |
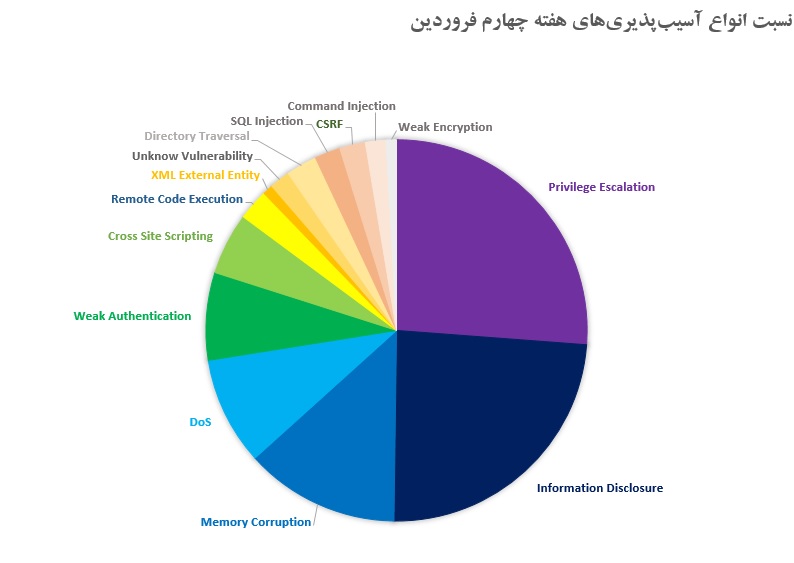
همچنین بیشترین نوع آسیبپذیریها، ارتقاء امتیاز و افشای اطلاعات بود.