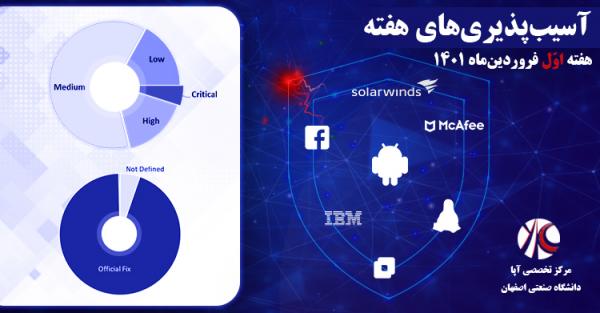
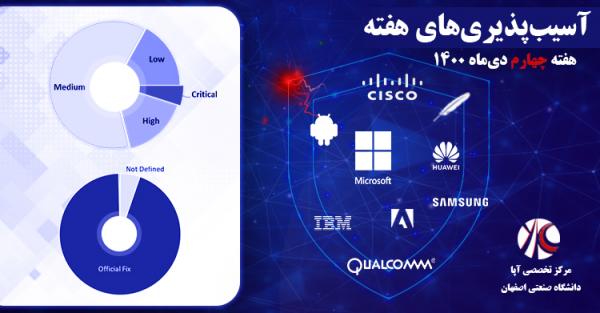
آسیبپذیریهای حیاتی هفته دوم بهمنماه

این هفته نیز مانند هفتۀ گذشته، آسیبپذیریهای زیادی با سطح خطر حیاتی در سوئیچهای مهم سیسکو شناسایی شدند. محصولات مهم دیگری مثل TP-LINK TL-WR849N، ضدهرزنامۀ Apache، نرمافزار محبوب OpenSMTPD و برنامۀ Sudo سیستمهای یونیکسی نیز آسیبپذیریهای مهم و با سطح خطر حیاتی داشتند. همچنین چندین آسیبپذیری خطرناک در پردازندههای اینتل و کرنل لینوکس از نوع تخریب حافظه وجود داشت که برای مهاجم امکان دسترسی به اطلاعات حساس سیستم را فراهم میکرد.
|
نوع آسیبپذیری |
محصول آسیبپذیر |
شناسۀ آسیبپذیری |
|
cross site request forgery |
Adive Framework |
CVE-2020-7991 |
|
cross site scripting |
Adive Framework |
CVE-2020-7990 |
|
cross site scripting |
Adive Framework |
CVE-2020-7989 |
|
information disclosure |
Apache Jackrabbit Oak Password |
CVE-2020-1940 |
|
information disclosure |
Apache NiFi Parameter Parser |
CVE-2020-1928 |
|
cross site scripting |
Apache NiFi UI |
CVE-2020-1933 |
|
information disclosure |
Apache Superset API Endpoint Credentials |
CVE-2020-1932 |
|
privilege escalation |
Apache SpamAssassin |
CVE-2020-1931 |
|
privilege escalation |
Apache SpamAssassin Rule Configuration |
CVE-2020-1930 |
|
cross site scripting |
Asus WRT-AC66U 3 RT Parental Control |
CVE-2020-7997 |
|
privilege escalation |
Avast Secure Browser Update Check AvastBrowserUpdate.exe |
CVE-2019-17190 |
|
directory traversal |
AVB MOTU |
CVE-2020-8009 |
|
memory corruption |
Belkin WeMo Insight Switch libbelkin_api.so |
CVE-2019-17094 |
|
privilege escalation |
BitDefender AV BDLDaemon |
CVE-2019-17103 |
|
command injection |
BitDefender BOX 2 API download_image |
CVE-2019-17095 |
|
privilege escalation |
BitDefender BOX 2 API update_setup |
CVE-2019-17102 |
|
command injection |
BitDefender BOX 2 Bootstrap get_image_url() |
CVE-2019-17096 |
|
privilege escalation |
BitDefender Endpoint Security Tools EPSecurityService.exe |
CVE-2019-17099 |
|
privilege escalation |
BitDefender Total Security 2020 bdserviceshost.exe |
CVE-2019-17100 |
|
denial of service |
BitDefender Total Security 2020 Junction Delete |
CVE-2020-8095 |
|
privilege escalation |
BitDefender Antivirus AntivirusforMac |
CVE-2020-8093 |
|
privilege escalation |
Biscom Secure File Transfer File Upload |
CVE-2020-8503 |
|
denial of service |
Cisco Small Business Switches |
CVE-2020-3147 |
|
information disclosure |
Cisco Small Business Switches |
CVE-2019-15993 |
|
Cross-Site Request Forgery |
Cisco Small Business Smart and Managed Switches |
CVE-2019-12636 |
|
privilege escalation |
Cisco Application Policy Infrastructure Controller OOB Management Interface |
CVE-2020-3139 |
|
denial of service |
Cisco Email Security Appliance ZIP Decompression Engine Restart |
CVE-2020-3134 |
|
cross site scripting |
Cisco Jabber Guest Web-based Management Interface |
CVE-2020-3136 |
|
weak authentication |
Cisco Webex Meetings Suite/Webex Meetings Online |
CVE-2020-3142 |
|
cross site request forgery |
Code Snippets Plugin Import Menu |
CVE-2020-8417 |
|
unknown vulnerability |
CPython Dependency Load api-ms-win-core-path-l1-1-0.dll |
CVE-2020-8315 |
|
cross site request forgery |
Cups Easy passwordmychange.php |
CVE-2020-8424 |
|
cross site request forgery |
Cups Easy userdelete.php |
CVE-2020-8425 |
|
privilege escalation |
D-Link DIR-859 urn cgibin ssdpcgi() |
CVE-2019-20215 CVE-2019-20217 |
|
privilege escalation |
D-Link DIR-859 cgibin ssdpcgi() |
CVE-2019-20216 |
|
cross site scripting |
Dolibarr ERP CRM |
CVE-2020-7994 |
|
cross site scripting |
Dolibarr ERP CRM passwordforgotten.php |
CVE-2020-7996 |
|
weak authentication |
Dolibarr ERP CRM |
CVE-2020-7995 |
|
privilege escalation |
ENS Trapdoor |
CVE-2020-5232 |
|
denial of service |
Feedgen XML |
CVE-2020-5227 |
|
cross site scripting |
Fortinet FortiSIEM Device Maintenance Schedule Stored |
CVE-2019-17651 |
|
privilege escalation |
FusionAuth E-Mail Template OS |
CVE-2020-7799 |
|
information disclosure |
GitLab Community Edition/Enterprise Edition Access Control |
CVE-2019-15590 |
|
information disclosure |
GitLab Community Edition/Enterprise Edition API |
CVE-2019-15583 |
|
information disclosure |
GitLab Community Edition/Enterprise Edition Email Link |
CVE-2019-15578 |
|
denial of service |
GitLab Community Edition/Enterprise Edition Epic Comment |
CVE-2019-5472 |
|
information disclosure |
GitLab Community Edition/Enterprise Edition |
CVE-2019-15581 |
|
privilege escalation |
GitLab Community Edition/Enterprise Edition Mattermost Command |
CVE-2019-5468 |
|
information disclosure |
GitLab Community Edition/Enterprise Edition Merge Request |
CVE-2019-5466 |
|
cross site scripting |
GitLab Community Edition/Enterprise Edition Mermaid Plugin |
CVE-2019-15586 |
|
information disclosure |
GitLab Community Edition/Enterprise Edition Milestone |
CVE-2019-15579 |
|
information disclosure |
GitLab Community Edition/Enterprise Edition Move Issue |
CVE-2019-5465 |
|
privilege escalation |
GitLab Community Edition/Enterprise Edition |
CVE-2019-15582 |
|
privilege escalation |
GitLab Community Edition/Enterprise Edition SAML |
CVE-2019-15585 |
|
information disclosure |
GitLab Community Edition/Enterprise Edition Security Dashboard |
CVE-2019-5470 |
|
privilege escalation |
GitLab Community Edition/Enterprise Edition Token |
CVE-2019-5462 |
|
|
GitLab Community Edition/Enterprise Edition url_blocker.rb Server-Side Request Forgery |
CVE-2019-5464 |
|
privilege escalation |
GitLab Enterprise Edition Merge Request |
CVE-2019-5474 |
|
memory corruption |
GNU Aspell libaspell.a |
CVE-2019-20433 |
|
Code Execution |
HP Business PCs Microsoft Windows 10 Kernel DMA Protection |
CVE-2019-18913 |
|
privilege escalation |
IBM Application Control Blacklist |
CVE-2019-4637 |
|
information disclosure |
IBM Content Navigator |
CVE-2019-4679 |
|
privilege escalation |
IBM MQ Appliance |
CVE-2019-4620 |
|
denial of service |
IBM MQ/MQ Appliance |
CVE-2019-4568 |
|
memory corruption |
IBM MQ/MQ Appliance Queue Manager Segmentation Fault |
CVE-2019-4614 |
|
XML External Entity |
IBM Security Access Manager Appliance XML Data |
CVE-2019-4707 |
|
command injection |
IBM Security Secret Server |
CVE-2019-4635 |
|
information disclosure |
IBM Security Secret Server CORS |
CVE-2019-4633 |
|
information disclosure |
IBM Security Secret Server Error Message |
CVE-2019-4636 |
|
information disclosure |
IBM Security Secret Server Man-in-the-Middle |
CVE-2019-4638 |
|
Open Redirect |
IBM Security Secret Server |
CVE-2019-4631 |
|
weak encryption |
IBM Security Secret Server |
CVE-2019-4639 |
|
cross site scripting |
IBM Security Secret Server Web UI |
CVE-2019-4632 |
|
memory corruption |
IBM Watson IoT Message Gateway |
CVE-2020-4207 |
|
XML External Entity |
IBM WebSphere Deployer Plugin XML Parser |
CVE-2020-2108 |
|
information disclosure |
Intel CPU Cleanup |
CVE-2020-0548 |
|
information disclosure |
Intel CPU Data Cache |
CVE-2020-0549 |
|
weak authentication |
Intellian Aptus FTP Default Credentials |
CVE-2020-8001 |
|
weak authentication |
Intellian Aptus |
CVE-2020-7999 |
|
weak authentication |
Intellian Aptus Web Default Credentials |
CVE-2020-8000 |
|
privilege escalation |
Jenkins REST API Endpoint Clickjacking |
CVE-2020-2105 |
|
information disclosure |
Jenkins JVM Memory Usage Chart |
CVE-2020-2104 |
|
information disclosure |
Jenkins Session Identifier |
CVE-2020-2103 |
|
information disclosure |
Jenkins HMAC Timing |
CVE-2020-2102 |
|
information disclosure |
Jenkins Comparison Timing |
CVE-2020-2101 |
|
denial of service |
Jenkins Service Port 33848 Amplification |
CVE-2020-2100 |
|
information disclosure |
Jenkins Inbound TCP Agent Protocol 3 Key |
CVE-2020-2099 |
|
cross site request forgery |
Joomla CMS Batch Action |
CVE-2020-8419 |
|
cross site scripting |
Joomla CMS com_actionlogs |
CVE-2020-8421 |
|
cross site request forgery |
Joomla CMS com_templates |
CVE-2020-8420 |
|
privilege escalation |
Ktor Proxy Request Smuggling |
CVE-2020-5207 |
|
cross site scripting |
Kronos Web Time and Attendance ApplicationBanner |
CVE-2020-8496 |
|
privilege escalation |
Kronos Web Time and Attendance com.threeis.webta.H491delegate Servlet |
CVE-2020-8495 |
|
privilege escalation |
Kronos Web Time and Attendance com.threeis.webta.H402editUser Servlet |
CVE-2020-8494 |
|
cross site scripting |
Kronos Web Time and Attendance com.threeis.webta.H261configMenu Servlet Stored |
CVE-2020-8493 |
|
denial of service |
Linux Kernel ip6_fib.c fib6_rule_lookup |
CVE-2019-20422 |
|
memory corruption |
Linux Kernel namei.c may_create_in_sticky |
CVE-2020-8428 |
|
information disclosure |
Linux Kernel KVM Hypervisor Memory |
CVE-2019-3016 |
|
command injection |
lsof Module exec |
CVE-2019-10783 |
|
denial of service |
Lustre File System mdt Module |
CVE-2019-20430 |
|
memory corruption |
Lustre File System mdt Module mdt_file_secctx_unpack |
CVE-2019-20432 |
|
denial of service |
Lustre File System mdt Module NULL Pointer Dereference |
CVE-2019-20424 |
|
memory corruption |
Lustre File System Packet lustre_msg_string |
CVE-2019-20425 |
|
memory corruption |
Lustre File System ptlrpc Module ldl_request_cancel |
CVE-2019-20428 |
|
memory corruption |
Lustre File System ptlrpc Module ldlm_cancel_hpreq_check |
CVE-2019-20426 |
|
memory corruption |
Lustre File System ptlrpc Module osd_map_remote_to_local |
CVE-2019-20431 |
|
memory corruption |
Lustre File System ptlrpc Module req_capsule_get_size |
CVE-2019-20427 |
|
memory corruption |
Lustre File System ptlrpc Module sptlrpc_svc_unwrap_request |
CVE-2019-20429 |
|
memory corruption |
Lustre File System ptlrpc Module target_handle_connect() |
CVE-2019-20423 |
|
privilege escalation |
mod_auth_ldap/mod_auth_ldap2 Prosody is_admin() |
CVE-2020-8086 |
|
memory corruption |
NetHack Configuration |
CVE-2020-5214 |
|
memory corruption |
NetHack Configuration |
CVE-2020-5213 |
|
memory corruption |
NetHack Configuration |
CVE-2020-5212 |
|
memory corruption |
NetHack Configuration |
CVE-2020-5211 |
|
memory corruption |
NetHack Options |
CVE-2020-5210 |
|
memory corruption |
NetHack Options |
CVE-2020-5209 |
|
weak authentication |
netprint App X.509 Certificate Man-in-the-Middle |
CVE-2020-5520 |
|
privilege escalation |
Netty Incomplete Fix CVE-2019-16869 HTTP Smuggling |
CVE-2020-7238 |
|
unknown vulnerability |
Netty HttpObjectDecoder.java |
CVE-2019-20444
CVE-2019-20445 |
|
cross site scripting |
node-red Stored |
CVE-2019-15607 |
|
memory corruption |
OpenJPEG t1.c opj_t1_clbl_decode_processor |
CVE-2020-8112 |
|
privilege escalation |
Opencast user-utils Endpoint |
CVE-2020-5231 |
|
privilege escalation |
Opencast Media Id.compact() |
CVE-2020-5230 |
|
weak encryption |
Opencast Password Hashing md5.json |
CVE-2020-5229 |
|
privilege escalation |
Opencast OAI-PMH |
CVE-2020-5228 |
|
weak encryption |
Opencast Cookie |
CVE-2020-5222 |
|
weak authentication |
Opencast Cookie |
CVE-2020-5206 |
|
privilege escalation |
OpenSMTPD SMTP Session smtp_session.c |
CVE-2020-7247 |
|
denial of service |
OSSEC-HIDS Log Server NULL Pointer Dereference |
CVE-2020-8448 |
|
memory corruption |
OSSEC-HIDS Log Server Use-After-Free |
CVE-2020-8447 |
|
directory traversal |
OSSEC-HIDS Log Server |
CVE-2020-8446 |
|
privilege escalation |
OSSEC-HIDS ossec-analysisd OS_CleanMSG |
CVE-2020-8445 |
|
memory corruption |
OSSEC-HIDS Log Server Use-After-Free |
CVE-2020-8444 |
|
memory corruption |
OSSEC-HIDS Log Server Off-By-One |
CVE-2020-8443 |
|
memory corruption |
OSSEC-HIDS Log Server Heap-based |
CVE-2020-8442 |
|
Code Execution |
Pandora FMS Filemanager Remote |
CVE-2019-20050 |
|
privilege escalation |
Pivotal tc Server/tc Runtimes JMX Socket Listener Man-in-the-Middle |
CVE-2019-11288 |
|
denial of service |
Python urllib.request.AbstractBasicAuthHandler |
CVE-2020-8492 |
|
information disclosure |
Rockwell Automation Arena Simulation Software |
CVE-2019-13521 |
|
information disclosure |
Rockwell Automation Arena Simulation Software |
CVE-2019-13519 |
|
command injection |
SMC Networks D3G0804W Network Diagnostic Tools formSetDiagnosticToolsFmPing |
CVE-2020-8087 |
|
information disclosure |
Solarwinds N-central Password |
CVE-2020-7984 |
|
memory corruption |
sudo pwfeedback tgetpass.c getln() |
CVE-2019-18634 |
|
privilege escalation |
Super File Explorer App File Upload |
CVE-2020-7998 |
|
information disclosure |
SuSE Linux Enterprise Server 15 yast2-rmt Log |
CVE-2018-20105 |
|
directory traversal |
SuSE Linux Enterprise Server obs-service-tar_scm |
CVE-2018-12476 |
|
privilege escalation |
Sylius Channel |
CVE-2020-5218 |
|
privilege escalation |
Sylius ResourceBundle |
CVE-2020-5220 |
|
cross site scripting |
Synacor Zimbra Collaboration Admin Console Reflected |
CVE-2019-12427 |
|
cross site scripting |
Synacor Zimbra Collaboration Persistent |
CVE-2019-8946 |
|
cross site scripting |
Synacor Zimbra Collaboration Persistent |
CVE-2019-8945 |
|
cross site scripting |
Synacor Zimbra Collaboration Persistent |
CVE-2019-11318 |
|
cross site scripting |
Synacor Zimbra Collaboration Reflected |
CVE-2019-8947 |
|
cross site scripting |
Synacor Zimbra Collaboration Reflected |
CVE-2019-15313 |
|
denial of service |
TensorFlow Eager Mode Segmentation Fault |
CVE-2020-5215 |
|
information disclosure |
TOTOLINK Realtek SDK Captcha formLogin |
CVE-2019-19825 |
|
privilege escalation |
TOTOLINK Realtek SDK formSysCmd |
CVE-2019-19824 |
|
weak encryption |
TOTOLINK/CIK TELECOM/KCTVJEJU/Hi-Wifi/HCN/T-broad Router Administration Interface Cleartext |
CVE-2019-19823 |
|
information disclosure |
TOTOLINK/CIK TELECOM/KCTVJEJU/Hi-Wifi/HCN/T-broad Router Administration Interface Config |
CVE-2019-19822 |
|
privilege escalation |
TP-LINK TL-WR849N Firmware softup |
CVE-2019-19143 |
|
cross site scripting |
TYPO3 svg.swf |
CVE-2020-8091 |
|
denial of service |
virglrenderer vrend_renderer.c |
CVE-2020-8003 |
|
denial of service |
virglrenderer vrend_renderer.c |
CVE-2020-8002 |
|
cross site scripting |
WSO2 API Manager API Documentation Reflected |
CVE-2019-20440 |
|
cross site scripting |
WSO2 API Manager API Documentation Reflected |
CVE-2019-20435 |
|
cross site scripting |
WSO2 API Manager API Documentation Stored |
CVE-2019-20438 |
|
cross site scripting |
WSO2 API Manager API Publisher Reflected |
CVE-2019-20439 |
|
cross site scripting |
WSO2 API Manager API Publisher Stored |
CVE-2019-20441 |
|
cross site scripting |
WSO2 API Manager Management Console Reflected |
CVE-2019-20434 |
|
cross site scripting |
WSO2 API Manager Registry UI Stored |
CVE-2019-20443 |
|
cross site scripting |
WSO2 API Manager Registry UI Stored |
CVE-2019-20442 |
|
cross site scripting |
WSO2 API Manager/IS as Key Manager/Identity Server Management Console |
CVE-2019-20437 |
|
cross site scripting |
WSO2 API Manager/IS as Key Manager/Identity Server Management Console |
CVE-2019-20436 |