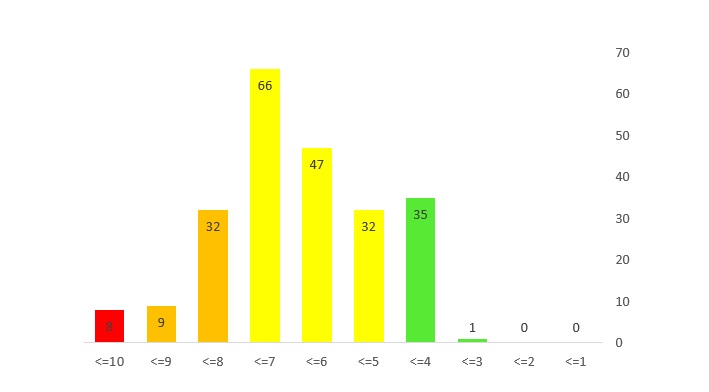
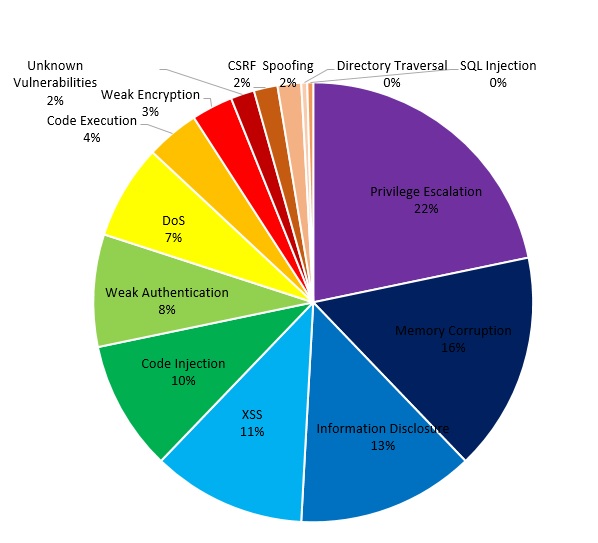
آسیبپذیریهای حیاتی هفته اول اردیبهشتماه

این هفته در محصولات بسیار مهم Foxit، IBM و Joomla! چندین آسیبپذیری با سطح خطر «حیاتی» و «بالا» شناسایی شده است. همچنین محصولات پرکاربرد شرکتهای D-Link و Netgear نیز چندین آسیبپذیری حیاتی داشتند. توزیع Ubuntu Linux نیز آسیبپذیری با سطح خطر «خطرناک» داشت.
|
نوع آسیبپذیری |
محصول آسیبپذیر |
شناسه آسیبپذیری |
|
Privilege Escalation |
ABB System 800xA Base Registry Permission |
CVE-2020-8474 |
|
XSS |
ABB System 800xA Information Manager Auxiliary Component |
CVE-2020-8477 |
|
Privilege Escalation |
ABB Telephone Gateway TG-S Access Control |
CVE-2019-19106 |
|
Information Disclosure |
ABB Telephone Gateway TG-S Configuration Page Password |
CVE-2019-19107 |
|
Weak Encryption |
ABB Telephone Gateway TG-S Settings and Config Plaintext |
CVE-2019-19105 |
|
Information Disclosure |
ABB Telephone Gateway TG-S Web Server |
CVE-2019-19104 |
|
XSS |
AirDisk Pro App |
CVE-2020-12131 |
|
XSS |
AirDisk Pro App |
CVE-2020-12130 |
|
XSS |
AirDisk Pro App |
CVE-2020-12129 |
|
XSS |
Anchor Content |
CVE-2020-12071 |
|
Privilege Escalation |
Apport apport |
CVE-2020-8831 |
|
Privilege Escalation |
Apport Crash Report TOCTOU |
CVE-2020-8833 |
|
XSS |
Atlassian Confluence Server Attachment Upload Stored |
CVE-2019-20102 |
|
Code Execution |
Beaker Sandbox |
CVE-2020-12079 |
|
Local File Inclusion |
BigBlueButton |
CVE-2020-12112 |
|
XSS |
BigBlueButton React dangerouslySetInnerHTML |
CVE-2020-12113 |
|
Privilege Escalation |
BitDefender Antivirus Free Quarantine |
CVE-2020-8099 |
|
Memory Corruption |
bson bson_ensure_space() |
CVE-2020-12135 |
|
XSS |
Catch Breadcrumb Plugin Reflected |
CVE-2020-12054 |
|
Information Disclosure |
CentralAuth Extension API |
CVE-2020-12051 |
|
XSS |
Ceph Object Gateway |
CVE-2020-1760 |
|
Denial of Service |
Ceph RGW Process NULL Pointer Dereference |
CVE-2020-12059 |
|
Information Disclosure |
Ceph Storage Dashboard |
CVE-2020-1699 |
|
Information Disclosure |
ColorOS screenShot |
CVE-2020-11828 |
|
Memory Corruption |
Contiki/Contiki-NG 6LoWPAN Fragment sicslowpan.c |
CVE-2019-9183 |
|
Memory Corruption |
Contiki/Contiki-NG 6LoWPAN Fragment sicslowpan.c |
CVE-2019-8359 |
|
Privilege Escalation |
CSV |
CVE-2020-12074 |
|
CSRF |
data-tables-generator-by-supsystic Plugin Ajax Stored |
CVE-2020-12076 |
|
unknown vulnerability |
data-tables-generator-by-supsystic Plugin Capability Check |
CVE-2020-12075 |
|
Weak Authentication |
D-Link DIR-615 T1 CAPTCHA Protection Mechanism |
CVE-2019-17525 |
|
Weak Authentication |
D-Link DSL-2640B B2 CGI Module |
CVE-2020-9277 |
|
Weak Authentication |
D-Link DSL-2640B B2 Management Interface Default Admin Password |
CVE-2020-9279 |
|
Denial of Service |
D-Link DSL-2640B B2 Reset |
CVE-2020-9278 |
|
Information Disclosure |
D-Link DSL-2640B B2 UDP Service Port 65002 Credentials |
CVE-2020-9275 |
|
Memory Corruption |
D-Link DSL-2640B B2 Web Server do_cgi() |
CVE-2020-9276 |
|
directory traversal |
Dong Joo Cho File Transfer iFamily |
CVE-2020-12128 |
|
Privilege Escalation |
EcoStruxure Machine Expert Downstream Component |
CVE-2020-7489 |
|
Code Execution |
Elementor File Upload |
CVE-2020-7055 |
|
Denial of Service |
Flexera FlexNet Publisher Command lmadmin.exe |
CVE-2019-8960 |
|
Denial of Service |
Flexera FlexNet Publisher lmadmin.exe |
CVE-2019-8961 |
|
Memory Corruption |
Foxit PhantomPDF Communication API Type Confusion |
CVE-2020-10908 |
|
Memory Corruption |
Foxit PhantomPDF Communication API AddWatermark |
CVE-2020-10909 |
|
Privilege Escalation |
Foxit PhantomPDF Communication API CombineFiles |
CVE-2020-10892 |
|
Privilege Escalation |
Foxit PhantomPDF Communication API ConvertToPDF |
CVE-2020-10890 |
|
Memory Corruption |
Foxit PhantomPDF Communication API GetFieldValue |
CVE-2020-10911 |
|
Memory Corruption |
Foxit PhantomPDF Communication API OCRAndExportToExcel |
CVE-2020-10913 |
|
Memory Corruption |
Foxit PhantomPDF Communication API RotatePage |
CVE-2020-10910 |
|
Memory Corruption |
Foxit PhantomPDF Communication API SetFieldValue |
CVE-2020-10912 |
|
Memory Corruption |
Foxit PhantomPDF Communication API Type Confusion |
CVE-2020-10891 |
|
Memory Corruption |
Foxit PhantomPDF Communication API Type Confusion |
CVE-2020-10889 |
|
Memory Corruption |
Foxit PhantomPDF U3D Object Heap-based |
CVE-2020-10896 |
|
Information Disclosure |
Foxit PhantomPDF U3D Object |
CVE-2020-10905 |
|
Information Disclosure |
Foxit PhantomPDF U3D Object |
CVE-2020-10903 |
|
Information Disclosure |
Foxit PhantomPDF U3D Object |
CVE-2020-10901 |
|
Information Disclosure |
Foxit PhantomPDF U3D Object |
CVE-2020-10894 |
|
Memory Corruption |
Foxit PhantomPDF U3D Object |
CVE-2020-10904 |
|
Memory Corruption |
Foxit PhantomPDF U3D Object |
CVE-2020-10902 |
|
Memory Corruption |
Foxit PhantomPDF U3D Object |
CVE-2020-10898 |
|
Memory Corruption |
Foxit PhantomPDF U3D Object |
CVE-2020-10893 |
|
Privilege Escalation |
Foxit PhantomPDF U3D Object |
CVE-2020-10897 |
|
Privilege Escalation |
Foxit PhantomPDF U3D Object |
CVE-2020-10895 |
|
Privilege Escalation |
Foxit Reader AcroForm |
CVE-2020-10900 |
|
Privilege Escalation |
Foxit Reader resetForm |
CVE-2020-10906 |
|
Privilege Escalation |
Foxit Reader XFA Form |
CVE-2020-10907 |
|
Privilege Escalation |
Foxit Reader XFA Template |
CVE-2020-10899 |
|
Privilege Escalation |
GitLab Community Edition/Enterprise Edition Artifact Upload Request Smuggling |
CVE-2020-11506 |
|
Privilege Escalation |
GitLab Community Edition/Enterprise Edition Group |
CVE-2020-11649 |
|
Information Disclosure |
GitLab Community Edition/Enterprise Edition Request Smuggling |
CVE-2020-11505 |
|
Privilege Escalation |
Google Earth Pro Windows Installer |
CVE-2020-8895 |
|
XSS |
GTranslate Plugin Reflected |
CVE-2020-11930 |
|
Weak Authentication |
HCL AppScan Enterprise Default Credentials |
CVE-2019-4327 |
|
Information Disclosure |
HCL Connections Stack-based |
CVE-2020-4085 |
|
XSS |
HPE Onboard Administrator Reflected |
CVE-2020-7132 |
|
Information Disclosure |
Huawei Honor V20 |
CVE-2020-1803 |
|
Information Disclosure |
Huawei Taurus-AL00B |
CVE-2020-9070 |
|
Information Disclosure |
IBM MaaS360 Agent |
CVE-2019-4735 |
|
Privilege Escalation |
IBM MaaS360 |
CVE-2020-4353 |
|
Memory Corruption |
IBM Spectrum Protect Stack-based |
CVE-2020-4415 |
|
Privilege Escalation |
IBM Tivoli Monitoring DLL |
CVE-2020-4311 |
|
Weak Encryption |
IBM UrbanCode Deploy Credentials |
CVE-2019-4668 |
|
Spoofing |
IBM UrbanCode Deploy Distributed Front End Impersonation |
CVE-2020-4202 |
|
Denial of Service |
InstallBuilder AutoUpdate Tool/Installer Billion Laughs |
CVE-2020-3946 |
|
Privilege Escalation |
IQrouter Access Control |
CVE-2020-11967 |
|
Remote Code Execution |
IQrouter Bash Shell |
CVE-2020-11963 |
|
Privilege Escalation |
IQrouter Lua diag_set_password |
CVE-2020-11964 |
|
Privilege Escalation |
IQrouter Lua reset_password |
CVE-2020-11966 |
|
Weak Authentication |
IQrouter SSH Service Default Admin Password |
CVE-2020-11965 |
|
Information Disclosure |
IQrouter web-panel |
CVE-2020-11968 |
|
Weak Encryption |
JetBrains GoLand Plugin Repository HTTP |
CVE-2020-11685 |
|
Spoofing |
JetBrains Hub OAuth Error Message |
CVE-2020-11691 |
|
Spoofing |
JetBrains IntelliJ IDEA License Server |
CVE-2020-11690 |
|
XSS |
JetBrains Space Chat Stored |
CVE-2020-11416 |
|
Weak Authentication |
JetBrains Space Password Authentication |
CVE-2020-11796 |
|
Weak Authentication |
JetBrains Space Session Timeout |
CVE-2020-11795 |
|
Information Disclosure |
JetBrains TeamCity Password |
CVE-2020-11687 |
|
Information Disclosure |
JetBrains TeamCity Server Setting |
CVE-2020-11686 |
|
Weak Authentication |
JetBrains TeamCity Session |
CVE-2020-11688 |
|
Privilege Escalation |
JetBrains TeamCity Setting |
CVE-2020-11689 |
|
unknown vulnerability |
JetBrains TeamCity |
CVE-2020-11938 |
|
Information Disclosure |
JetBrains YouTrack EB Export |
CVE-2020-11692 |
|
Denial of Service |
JetBrains YouTrack TIFF File |
CVE-2020-11693 |
|
Privilege Escalation |
Joomla CMS ACL |
CVE-2020-11890 |
|
Denial of Service |
Joomla CMS com_users |
CVE-2020-11889 |
|
Privilege Escalation |
Joomla CMS com_users |
CVE-2020-11891 |
|
XSS |
jQuery IMG Element |
CVE-2018-18405 |
|
Privilege Escalation |
Juplink RX4-1500 httpd setup3.htm |
CVE-2020-8798 |
|
Privilege Escalation |
Juplink RX4-1500 Linux Subsystem exec |
CVE-2020-8797 |
|
Memory Corruption |
libming decompile.c decompileIF() |
CVE-2020-11895 |
|
Memory Corruption |
libming decompile.c decompileIF() |
CVE-2020-11894 |
|
Denial of Service |
libslirp ip_input.c ip_reass() |
CVE-2020-1983 |
|
Memory Corruption |
LibVNCServer cursor.c HandleCursorShape |
CVE-2019-20788 |
|
Weak Authentication |
MailStore Outlook Add-in/Email Archive Outlook Add-in Certificate |
CVE-2020-11806 |
|
Privilege Escalation |
mappress-google-maps-for-wordpress Plugin Ajax |
CVE-2020-12077 |
|
Remote Code Execution |
media-library-assistant Plugin mla_gallery |
CVE-2020-11928 |
|
Weak Authentication |
MinIO Admin API |
CVE-2020-11012 |
|
Weak Authentication |
Modicon Controller Communication Module Default Credentials |
CVE-2019-6859 |
|
Weak Encryption |
Modicon M218/M241/M251/M258 Cleartext |
CVE-2020-7488 |
|
Code Execution |
Modicon M218/M241/M251/M258 |
CVE-2020-7487 |
|
Privilege Escalation |
MSI True Color Unquoted Search Path |
CVE-2020-8842 |
|
Memory Corruption |
nDPI SSH Protocol Dissector ssh.c |
CVE-2020-11939 |
|
Information Disclosure |
nDPI SSH Protocol ssh.c |
CVE-2020-11940 |
|
Command Injection |
Netatmo Smart Indoor Camera |
CVE-2019-17101 |
|
Privilege Escalation |
Netgear D3600/D6000 Configuration |
CVE-2018-21138 |
|
unknown vulnerability |
Netgear D3600/D6000 Configuration |
CVE-2018-21140 |
|
Weak Authentication |
Netgear D3600/D6000 Default Credentials |
CVE-2018-21137 |
|
Information Disclosure |
Netgear D3600/D6000 |
CVE-2018-21136 |
|
Command Injection |
Netgear D7800/R7500v2/R7800/R8900/R9000 |
CVE-2018-21112 |
|
Command Injection |
Netgear D7800/R7800/R8900/R9000/WNDR4300v2/WNDR4500v3 |
CVE-2018-21146 |
|
Privilege Escalation |
Netgear D7800/R7800/R9000 Configuration |
CVE-2018-21161 |
|
Memory Corruption |
Netgear D8500 Stack-based |
CVE-2018-21134 |
|
Denial of Service |
Netgear GS110EMX/GS810EMX/XS512EM/XS724EM |
CVE-2018-21122 |
|
Information Disclosure |
Netgear GS810EMX |
CVE-2018-21143 |
|
Weak Authentication |
Netgear GS810EMX/XS512EM/XS724EM |
CVE-2018-21121 |
|
Memory Corruption |
Netgear R2000 Stack-based |
CVE-2018-21135 |
|
Command Injection |
Netgear R6220/WNDR3700v5 |
CVE-2018-21164 |
|
Information Disclosure |
Netgear R7300 |
CVE-2018-21139 |
|
Command Injection |
Netgear R7800 |
CVE-2018-21110 |
|
Command Injection |
Netgear R7800 |
CVE-2018-21109 |
|
Command Injection |
Netgear R7800 |
CVE-2018-21108 |
|
Command Injection |
Netgear R7800 |
CVE-2018-21107 |
|
Command Injection |
Netgear R7800 |
CVE-2018-21106 |
|
Command Injection |
Netgear R7800 |
CVE-2018-21105 |
|
Command Injection |
Netgear R7800 |
CVE-2018-21104 |
|
Command Injection |
Netgear R7800 |
CVE-2018-21103 |
|
Command Injection |
Netgear R7800 |
CVE-2018-21101 |
|
CSRF |
Netgear ReadyNAS |
CVE-2018-21160 |
|
CSRF |
Netgear ReadyNAS |
CVE-2018-21102 |
|
Command Injection |
Netgear WAC505/WAC510 |
CVE-2018-21130 |
|
Command Injection |
Netgear WAC505/WAC510 |
CVE-2018-21127 |
|
Command Injection |
Netgear WAC505/WAC510 |
CVE-2018-21126 |
|
Command Injection |
Netgear WAC505/WAC510 |
CVE-2018-21119 |
|
Privilege Escalation |
Netgear WAC505/WAC510 Firmware Downgrade |
CVE-2018-21131 |
|
Information Disclosure |
Netgear WAC505/WAC510 |
CVE-2018-21129 |
|
Weak Authentication |
Netgear WAC505/WAC510 |
CVE-2018-21132 |
|
Weak Authentication |
Netgear WAC505/WAC510 |
CVE-2018-21128 |
|
Memory Corruption |
Netgear WAC505/WAC510/WAC720/WAC730/WAC740/WND930 Stack-based |
CVE-2018-21133 |
|
Privilege Escalation |
Netgear WAC510 |
CVE-2018-21124 |
|
Weak Authentication |
Netgear WAC510 |
CVE-2018-21125 |
|
Command Injection |
Netgear WC7500/WC7520/WC7600v1/WC7600v2 |
CVE-2018-21123 |
|
CSRF |
Netgear WN604 |
CVE-2018-21120 |
|
Memory Corruption |
Netgear WNDR3400v3 Stack-based |
CVE-2018-21163 |
|
Command Injection |
Netgear WNDR4500v3 |
CVE-2018-21114 |
|
Command Injection |
Netgear WNDR4500v3 |
CVE-2018-21113 |
|
Memory Corruption |
Netgear WNDR4500v3 |
CVE-2018-21151 |
|
Memory Corruption |
Netgear WNDR4500v3 Stack-based |
CVE-2018-21147 |
|
Denial of Service |
Netgear WNR2000v5 |
CVE-2018-21166 |
|
Denial of Service |
Netgear WNR2000v5 |
CVE-2018-21165 |
|
Denial of Service |
Netgear WNR2000v5 |
CVE-2018-21142 |
|
Denial of Service |
Netgear WNR2000v5 |
CVE-2018-21141 |
|
Memory Corruption |
Netgear WNR2000v5 Stack-based |
CVE-2018-21150 |
|
Memory Corruption |
Netgear WNR2000v5 Stack-based |
CVE-2018-21111 |
|
Memory Corruption |
Netgear WNR2000v5 Stack-based |
CVE-2018-21148 |
|
Memory Corruption |
Netgear WNR2000v5 Stack-based |
CVE-2018-21145 |
|
Memory Corruption |
Netgear WNR2000v5 Stack-based |
CVE-2018-21144 |
|
Command Injection |
Netgear WNR3500Lv2 |
CVE-2018-21162 |
|
Code Execution |
Netgear XR500 |
CVE-2018-21116 |
|
Code Execution |
Netgear XR500 |
CVE-2018-21115 |
|
Code Execution |
Netgear XR500 Traceroute |
CVE-2018-21117 |
|
Weak Authentication |
Netgear XR500 |
CVE-2018-21118 |
|
Weak Encryption |
Nginx Controller Agent Installer Script install.sh |
CVE-2020-5867 |
|
Privilege Escalation |
Nginx Controller helper.sh |
CVE-2020-5866 |
|
Weak Encryption |
Nginx Controller Postgres Database Server Man-in-the-Middle |
CVE-2020-5865 |
|
Weak Encryption |
Nginx Controller TLS |
CVE-2020-5864 |
|
Denial of Service |
OPC Foundation UA .NET Standard |
CVE-2020-8867 |
|
Weak Authentication |
OpenConnect X509_check_ |
CVE-2020-12105 |
|
Information Disclosure |
Openshift Container Platform Log |
CVE-2020-10712 |
|
Denial of Service |
OpenSSL TLS 1.3 Handshake SSL_check_chain() |
CVE-2020-1967 |
|
Privilege Escalation |
paypal-adaptive Prototype |
CVE-2020-7643 |
|
Privilege Escalation |
Phproject File Upload |
CVE-2020-11011 |
|
Privilege Escalation |
Pion DTLS conn.go handleIncomingPacket |
CVE-2019-20786 |
|
Privilege Escalation |
Plex Media Server Python Code |
CVE-2020-5740 |
|
Information Disclosure |
PrestaShop Access Control |
CVE-2020-5287 |
|
Information Disclosure |
PrestaShop Access Control |
CVE-2020-5279 |
|
XSS |
PrestaShop AdminAttributesGroups Page Reflected |
CVE-2020-5265 |
|
XSS |
PrestaShop AdminCarts Page Reflected |
CVE-2020-5276 |
|
XSS |
PrestaShop AdminFeatures Page Reflected |
CVE-2020-5269 |
|
XSS |
PrestaShop |
CVE-2020-5270 |
|
XSS |
PrestaShop Dashboard Page Reflected |
CVE-2020-5271 |
|
XSS |
PrestaShop Exception Page Reflected |
CVE-2020-5278 |
|
Information Disclosure |
PrestaShop Product Attributes Page |
CVE-2020-5288 |
|
Privilege Escalation |
PrestaShop Product Page |
CVE-2020-5293 |
|
XSS |
PrestaShop Reflected |
CVE-2020-5285 |
|
XSS |
PrestaShop Reflected |
CVE-2020-5264 |
|
XSS |
PrestaShop Search Page Reflected |
CVE-2020-5272 |
|
XSS |
PrestaShop Upload Reflected |
CVE-2020-5286 |
|
XSS |
python-markdown2 Element Name |
CVE-2020-11888 |
|
Command Injection |
Rapid7 Metasploit Framework libnotify Plugin |
CVE-2020-7350 |
|
Memory Corruption |
re2c scanner.cc fill |
CVE-2020-11958 |
|
Privilege Escalation |
responsive-add-ons Plugin Access Control |
CVE-2020-12073 |
|
Privilege Escalation |
Sonatype Nexus Repository Manager UI/API |
CVE-2020-11753 |
|
Weak Authentication |
Squid Web Proxy Digest Authentication Nonce handler Replay |
CVE-2020-11945 |
|
Privilege Escalation |
SysAid On-Premise AJP Protocol GhostCat |
CVE-2020-10569 |
|
Denial of Service |
Teeworlds server.cpp SendMsg |
CVE-2020-12066 |
|
Memory Corruption |
Teeworlds Tilemap Size Integer Overflow |
CVE-2019-20787 |
|
Privilege Escalation |
Thoshiba Canvio Premium 3TB HDD Password tool |
CVE-2020-5569 |
|
SQL Injection |
Tortoise ORM Mass Update |
CVE-2020-11010 |
|
Memory Corruption |
Ubuntu Linux Overlayfs/shiftfs call_mmap() |
CVE-2019-15794 |
|
Information Disclosure |
Ubuntu Linux shiftfs |
CVE-2019-15793 |
|
Memory Corruption |
Ubuntu Linux shiftfs shiftfs_btrfs_ioctl_fd_replace() |
CVE-2019-15791 |
|
Privilege Escalation |
Ubuntu Linux shiftfs shiftfs_btrfs_ioctl_fd_replace() |
CVE-2019-15792 |
|
Privilege Escalation |
Undertow Servlet Container |
CVE-2020-1757 |
|
Privilege Escalation |
Veeam one Agent HandshakeResult |
CVE-2020-10915 |
|
Privilege Escalation |
Veeam one Agent PerformHandshake |
CVE-2020-10914 |
|
Privilege Escalation |
Vesta Control Panel Cron Job |
CVE-2020-10786 |
|
Privilege Escalation |
Vesta Control Panel v-change-user-password |
CVE-2020-10787 |
|
Code Execution |
Vijeo Designer Basic |
CVE-2020-7490 |
|
Information Disclosure |
Zoho ManageEngine ManageEngine OpManager Servlet Call Key |
CVE-2020-11946 |
|
XSS |
Zulip Server |
CVE-2020-9445 |
|
XSS |
Zulip Server |
CVE-2020-10935 |
|
unknown vulnerability |
Zulip Server |
CVE-2020-9444 |